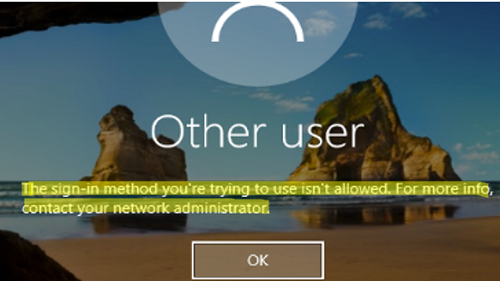
If you see The sign-in method is not allowed error when trying to logon Windows, it means that the resulting Group Policy settings prevent local sign-in for a current user account. Most often the error appears if you try to sign in to a computer using a guest account or to a domain controller using a user account without domain administrator privileges. However, there may be some other reasons.
The sign-in method you're trying to use isn't allowed. For more info, contact your network administrator.
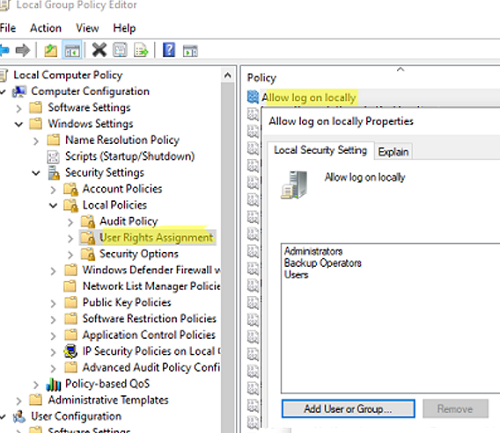
The list of users and groups that are allowed to interactively sign in to a computer is configured using GPO.
- Open the Local Group Policy Editor (
gpedit.msc); - Go to Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> User Rights Assignment;
- Find Allow log on locally in the list of policies;
- The policy contains the list of groups and users allowed to sign in to the computer locally. Depending on the operating system and computer role, the list of groups allowed to sign in locally may vary. For example, local sign-in is allowed for the following user groups on workstations running Windows 10 and servers running Windows Server 2022,2019,2016:
- Administrators
- Backup Operators
- Users
On servers running Windows Server with the Active Directory domain controller role (ADDS), interactive sign-in is allowed for the following groups:
- Account Operators
- Administrators
- Backup Operators
- Print Operators
- Server Operators
- You can allow local sign-in for other users or groups. To do it, click Add User or Group and select the users you want to add. For example, you prevent non-admin users from logging on to the device. To do it, just remove the Users group from the policy settings;
- After making the changes, update the Group Policy settings using the
gpupdate /forcecommand (no reboot required).
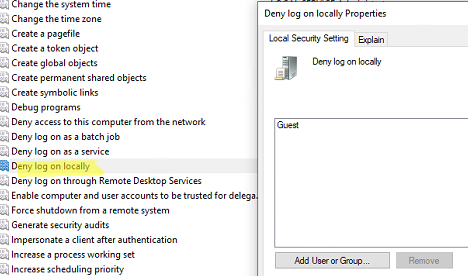
Also, note that there is another policy to prevent local interactive sign-in to Windows in the same GPO section. The policy is called Deny log on locally. In my case, anonymous local logon under the Guest account is denied on the computer.
You can prevent a specific group (or a user) from logging on to the computer locally by adding them to this policy. Since Deny log on locally policy has a higher priority than Allow log on locally, users won’t be able to log on to a computer with the following error:
The sign-in method isn’t allowed.
In a domain environment, multiple GPOs may be assigned to a computer. So to get the policies allowing local sign-in, you need to check the resulting policy settings. You can use the rsop.msc console or the gpresult tool to get the resulting GPO settings on your computer.
Another reason why you can see “The sign-in method you are trying to use isn’t allowed” error is when a list of computers a user is allowed to log on to is restricted in the LogonWorkstations user attribute in AD (read more here). Using the Get-ADUser PowerShell cmdlet, you can display a list of computers a user is allowed to log on to (by default, the list is empty):
(Get-ADUser maxbak -Properties LogonWorkstations).LogonWorkstations
In some cases, you may allow a user to log on to the domain controller/ Windows Server hosts over RDP or locally. It is enough to add a user account to the local policy Allow log on locally on your server. Anyway, it will be better than adding a user to the Local Administrators group. However, it is even better to use an RODC domain controller for security reasons.
You can also allow local logon using ntrights (the tool was included in some old Admin Pack versions). For example, to allow local logon for a domain group, run the command below:
ntrights +r SeInteractiveLogonRight -u "GroupName"
To deny local logon:
ntrights -r SeInteractiveLogonRight -u "UserName"