You can use the Get-ADComputer PowerShell cmdlet to get various information about computer account objects (servers and workstations) in an Active Directory domain. This is one of the most useful cmdlets for searching AD computers by various criteria
Suppose, your task is to find all inactive computers in Active Directory that have not been registered in a domain for more than 120 days and disable these computer accounts.
Before you can use the Get-ADComputer cmdlet, you must install and import the Active Directory Module for Windows PowerShell.
Import-Module activedirectory
Enable-WindowsOptionalFeature -Online -FeatureName RSATClient-Roles-AD-Powershell
List Computer Object Properties with Get-ADComputer
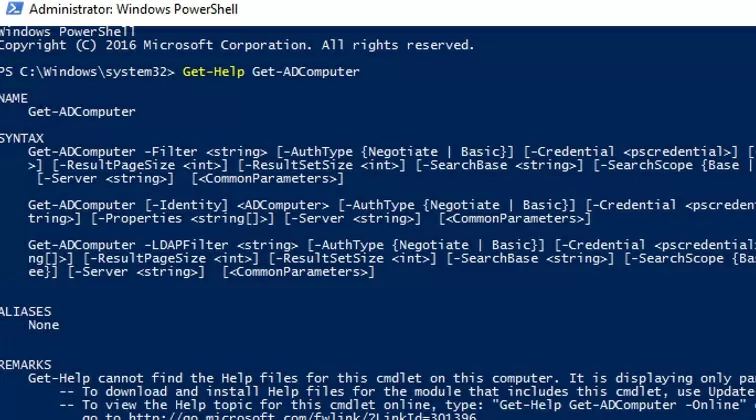
You can get help on Get-ADComputer cmdlet parameters as usual with the Get-Help command:
Get-Help Get-ADComputer
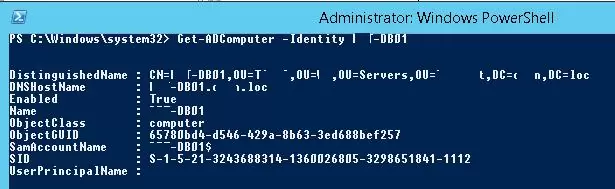
To get information about a specific computer account in the domain, specify its name as an argument of the -Identity parameter:
Get-ADComputer -Identity SRV-DB01
DistinguishedName : CN=SRV-DB01,OU=Servers,OU=London,OU=UK,DC=woshub,DC=com DNSHostName : SRV-DB01.woshub.com Enabled : True Name : SRV-DB01 ObjectClass : computer ObjectGUID : 87654321-1234-5678-0000-123412341234 SamAccountName : SRV-DB01$ SID : S-1-5-21-123456780-1234567890-0987654321-1234 UserPrincipalName :
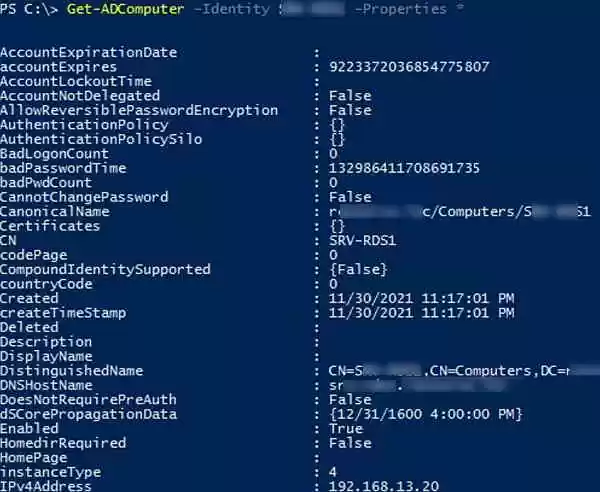
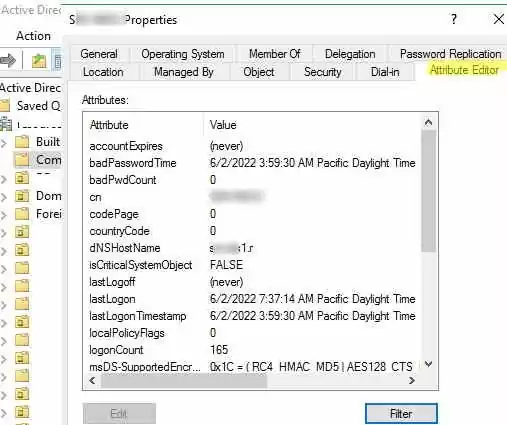
The cmdlet Get-ADComputer returned only the basic properties of the Computer object from AD. We are interested in the time of the last computer registration in the AD domain, but this information is not displayed in the output of the command above. You can list all available properties of this computer object from Active Directory:
Get-ADComputer -Identity SRV-DB01 -Properties *
This list of computer attributes is also available in the Active Directory Users and Computers console (dsa.msc) on the Attribute Editor tab.
Get-ADComputer -Filter * -Properties * | Get-Member
As you can see, the last logon time of this computer to the network is specified in the computer’s attribute LastLogonDate – 6/2/2022 3:53:50 AM.
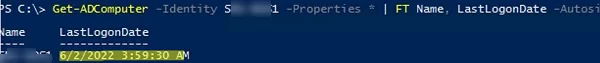
The Get-ADComputer cmdlet allows you to display any of the computer’s properties in the command results. Remove all unnecessary information, leaving only values of Name and LastLogonDate attributes in the output.
Get-ADComputer -identity SRV-DB01 -Properties * | FT Name, LastLogonDate -Autosize
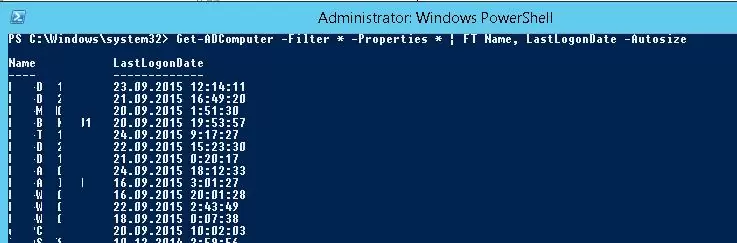
So, we received data on the last time of registration in the domain for a single computer. Then you have to modify the command to make it display the information about the time of the last network registration for all computers in the domain. To do it, replace –Identity to –Filter *:
Get-ADComputer -Filter * -Properties * | FT Name, LastLogonDate -Autosize
We got a simple table that contains only 2 fields: computer name and LastLogonData date. You can add other fields of the Computer object from AD to this table.
To display information about the computer objects in a particular OU (Organizational Unit), use the –SearchBase parameter:
Get-ADComputer -SearchBase ‘OU=Paris,DC=woshub,DC=loc’ -Filter * -Properties * | FT Name, LastLogonDate -Autosize
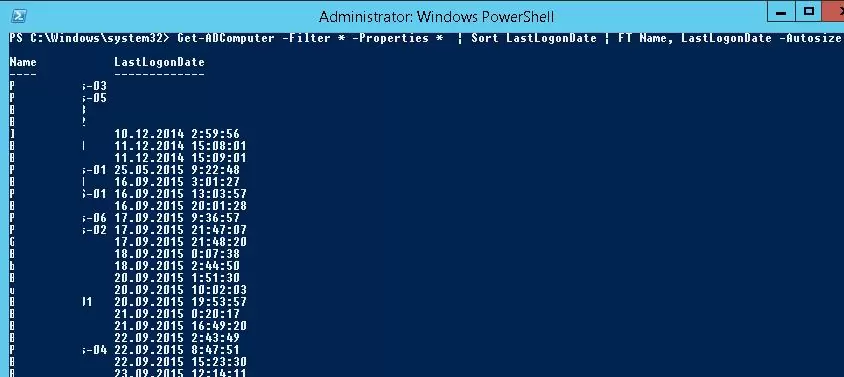
Sort the query results by the date of the last logon using the Sort cmdlet:
Get-ADComputer -Filter * -Properties * | Sort LastLogonDate | FT Name, LastLogonDate -Autosize
So, we have a list of domain computers and the date they last logged on to the Active Directory network. Now we want to disable the computer accounts that have not been used for more than 20 days.
Using Get-Date we can get the value of the current date in the variable and reduce it to 120 days:
$date_with_offset= (Get-Date).AddDays(-120)
The resulting date variable can be used as a filter of Get-ADComputer query in LastLogonDate field:
Get-ADComputer -Properties LastLogonDate -Filter {LastLogonDate -lt $date_with_offset } | Sort LastLogonDate | FT Name, LastLogonDate -Autosize
So we have got a list of inactive computer accounts that have not been registered on the domain network for more than 120 days. Use the Disable-ADAccount or Set-ADComputer command to disable these accounts.
Get-ADComputer -Properties LastLogonDate -Filter {LastLogonData -lt $date_with_offset } | Set-ADComputer -Enabled $false -whatif
Now you can disable all inactive computer accounts:
Get-ADComputer -Properties LastLogonDate -Filter {LastLogonData -lt $datecutoff} | Set-ADComputer -Enabled $false
Using Search Filters with Get-ADComputer
You can use the -Filter argument of the Get-ADComputer cmdlet to search for multiple Active Directory computers based on specific criteria. Here you can use wildcards and logical comparison operators. Only basic computer object attributes can be used as filters.
Below are some more useful examples of using the Get-ADComputer cmdlet to query and search computer objects in the domain by specific criteria.
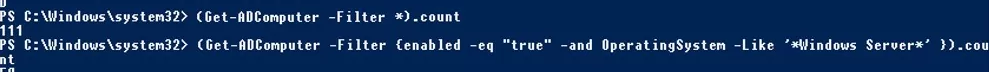
Get the total number of all active (unblocked) computers in Active Directory:
(Get-ADComputer -Filter {enabled -eq "true"}).count
You can use multiple filters to search for computers by several parameters at once. To do this, use PowerShell logical comparison operators (-and, -eq, -ne , -gt , -ge , -lt , -le , -like , -notlike , -and , -or , etc.).
Count the number of Windows Server hosts in the AD domain:
(Get-ADComputer -Filter {enabled -eq "true" -and OperatingSystem -Like '*Windows Server*' }).count
Get a list of computers in a specific OU whose names start with LonPC:
Get-ADComputer -Filter {Name -like "LonPC*"} -SearchBase ‘OU=London,DC=woshub,DC=com’ -Properties IPv4Address | Format-table Name,DNSHostName,IPv4Address | ft -Wrap –Auto
When searching in the OU, you can use the additional parameter -SearchScope 1, which means that you need to search only in the root OU. The -SearchScope 2 option means a recursive search for computers in all nested OUs.
To find all workstation computers running Windows 10:
Get-ADComputer -Filter {OperatingSystem -like '*Windows 10*'}
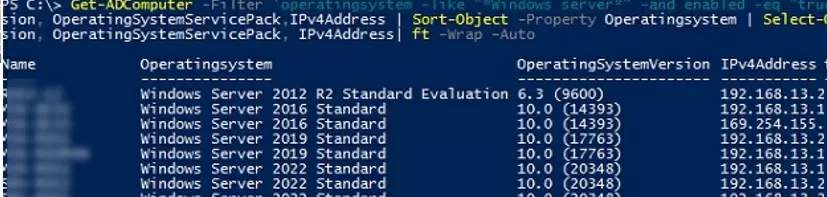
Get a list of servers in the domain with the OS version, Service Pack installed, and IP address:
Get-ADComputer -Filter 'operatingsystem -like "*Windows server*" -and enabled -eq "true"' -Properties Name,Operatingsystem, OperatingSystemVersion, OperatingSystemServicePack,IPv4Address | Sort-Object -Property Operatingsystem | Select-Object -Property Name,Operatingsystem, OperatingSystemVersion, OperatingSystemServicePack, IPv4Address| ft -Wrap –Auto
The output was such a clean table with a list of Windows Server in the AD:
Query Active Directory Commuters with Get-ADComputer: Examples
The following are some more useful examples of using the Get-ADComputer cmdlet to select computers in a domain based on certain criteria.
The -LDAPFilter attribute allows you to use various LDAP queries as a parameter of the Get-ADComputer cmdlet, for example:
Get-ADComputer -LDAPFilter "(name=*db*)"|ft
Find all disabled computer objects in a specific Active Directory OU:
Get-ADComputer -filter * -SearchBase ‘OU=Computers,OU=London,DC=woshub,dc=com’ | Where-Object {$_.enabled -eq $False}
To delete all computer accounts that have not been logged into the domain for more than 6 months, you can use the command:
Get-ADComputer -properties lastLogonDate -filter * | where { $_.lastLogonDate -lt (get-date).addmonths(-6) } | Remove-ADComputer
Display the time the computer’s password was last changed in Active Directory. By default, the password should be changed automatically by the computer once every 30 days. If the computer password doesn’t match the password in AD, the computer’s trust relationship with the domain will be broken:
Get-ADComputer –Identity MUNPC321 -Properties PasswordLastSet
The result of the Get-ADComputer command can be exported to a plain text file:
Get-ADComputer -Filter { OperatingSystem -Like '*Windows Server 2016*' } -Properties OperatingSystem | Select DNSHostName, OperatingSystem | Format-Table -AutoSize C:\Script\server_system.txt
You can also get a list of computers and export it to a CSV file:
Get-ADComputer -Filter * -Property * | Select-Object Name,OperatingSystem,OperatingSystemServicePack | Export-CSV All-Windows.csv -NoTypeInformation -Encoding UTF8
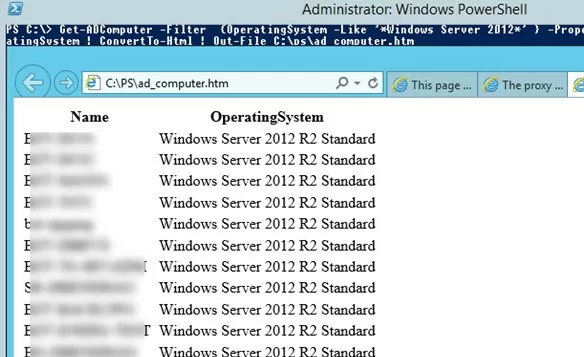
Or get an HTML report with a list of computers and necessary properties:
Get-ADComputer -Filter {OperatingSystem -Like '*Windows Server 2012*' } -Properties * | Select-Object Name,OperatingSystem | ConvertTo-Html | Out-File C:\ps\ad_computers_list.html
You can remotely query AD computers via WMI or CIM. For example, to display the serial numbers of all servers in the domain:
Get-ADComputer -Filter 'operatingsystem -like "*Windows server*" -and enabled -eq "true"' | Select-Object Name | Foreach-Object {Get-CimInstance Win32_Bios -ComputerName $_.Name -ErrorAction SilentlyContinue | Select-Object PSComputerName,SerialNumber}
To perform a specific action with all the computers from the resulting list, you must use the Foreach loop. In this example, we want to get a list of Windows Server hosts in the domain with model and manufacturer.
$Computers = Get-ADComputer -Filter {OperatingSystem -Like '*Windows Server*'}
Foreach ($Computer in $Computers)
{
$Hostname = $Computer.Name
$ComputerInfo = (Get-WmiObject -Computername $Hostname Win32_ComputerSystem)
$Manufacturer = $Computer.Manufacturer
$Model = $Computer.Model
Write-Host "Name: $Hostname"
Write-Host "Manufacturer: $Manufacturer"
Write-Host "Model: $Model"
Write-Host " "
$Content = "$Hostname;$Manufacturer;$Model"
Add-Content -Value $Content -Path "C:\PS\ServersInfo.txt"
}
You can use a shorter loop syntax. Suppose you need to run a specific command on all computers in a specific OU. In this example, I will use the Invoke-Command to run a group policy update command on all servers:
get-adcomputer -SearchBase "OU=Servers,DC=woshub,DC=com" -Filter * | %{ Invoke-Command -Computer $_.Name -ScriptBlock {gpupdate /force} }
Using Get-ADComputer and PowerShell startup scripts, you can control various computer settings or store various useful information in computer attributes in AD (for example, you can add a username to the computer description,).
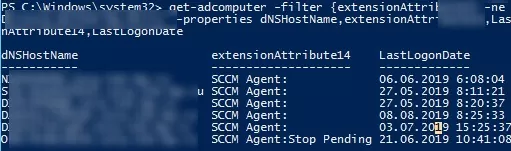
For example, I monitor the state of the SCCM agent on users’ computers. When each computer boots, it runs a small logon script which saves the ccmexec service status to an unused computer attribute – extensionAttribute10. Then, using the following command, I can find computers on which the CCMExec service is missing or not running.
get-adcomputer -filter {extensionAttribute10 -ne "SCCM Agent:Running"} -SearchBase “OU=Compters,OU=London,DC=woshub,DC=com” -properties dNSHostName,extensionAttribute10,LastLogonDate |select-object dNSHostName,extensionAttribute10,LastLogonDate
19 comments
When i run Get-ADComputer -Identity GM172Q13
it works
But when i run
Get-ADComputer -Identity GM172Q13 -Properties *
I get:
Get-ADComputer : One or more properties are invalid.
Parameter name: msDS-AssignedAuthNPolicy
At line:2 char:1
+ Get-ADComputer -Identity GM172Q13 -Properties *
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : InvalidArgument: (GM172Q13:ADComputer) [Get-ADComputer], ArgumentException
+ FullyQualifiedErrorId : ActiveDirectoryCmdlet:System.ArgumentException,Microsoft.ActiveDirectory.Management.Commands.GetADComputer
Any ideas?
Figured it out…. “This has been identified as a bug, and there’s a hotfix as described in KB2923122 that you can install. You could also install KB2928680 that contains the above hotfix, and others as well.”
Nice write-up !
Thanks for sharing this.
Here is another informative article which summarizes almost the similar concern and helps to find out inactive users & computer accounts in active directory. You can take further action to disable or remove them : http://activedirectorycleanup.blogspot.in/2014/08/find-inactive-users-compueters-inAD.html
Nice information.
Is there a way i can import a list of computer names (Desktops) from a text file that I have and query againts only that list of ADcomputers to check there last logon time stamp ?
When i lookup help for Get-ADcomputers , the -Identity parameter accepts pipeline binding only by value and not by Propertyname, henec i am not able to do it.
Is there a way you could suggest.
I am trying something like this
$name = Get-content -path c:\pclist.txt
ForEach-Object
{ Get-Adcomputer -Identity $name -properties * | Format-table name,created,lastlogon}
Hi,
Try to run the command below
get-content c:\pclist.txt | % {Get-ADComputer -Identity $_ -properties * | select name,created,lastlogon}
Correct the .txt file output to this:
PS C:\Users\dwalker2> Get-ADComputer -Filter { OperatingSystem -Like ‘*Windows Server*’ } -Properties OperatingSystem | Select Name, OperatingSystem | Format-Table -Autosize | Out-File C:\Script\server_systems.txt
When using an “Authenticated User” account, not a privileged account (i.e., a Domain Admin account), I’m unable to get the “OperatingSystem” attribute. Is there a method to retrieve the “OperatingSystem” attribute without using a “Domain Admin” or other ‘privileged’ account?
It’s pretty strange, by default, any domain user can get the value of this attribute
Great!
is there a way to tell which user(account) was last logged on?
The computer account in AD does not store info about the current user of the system. This can be done using additional logon script.
But you can find logged user remotely using WMI in the interactive mode:
Get-WmiObject –ComputerName PCNameHere –Class Win32_ComputerSystem | Select-Object UserName
Thanks Max
The Get-WMIObject is a great approach
[…] https://woshub.com/get-adcomputer-getting-active-directory-computers-info-via-powershell/ […]
Can u pls suggest me to get windows version of adcomputers using powershell command
Try this code:
get-adcomputer -filter * -properties *|select Name,OperatingSystem,OperatingSystemVersion |ft
Thank YOU very mutch that worked perfectly!
I have list of SAM account names and I need to confirm the OS version on these machines, is there any PS script to help me with this?
Save the list of computer names to a plain text file and run the following PS code to get the OS version:
get-content c:\ps\pclist.txt | % {Get-ADComputer -Identity $_ -properties * | select name,operatingSystem,operatingSystemVersion}
Hola, alguin puede ayudarme, necesito sacar un listado de todos los equipos de mi dominio y que cada equipo muestre la version de Bios que tiene instalada pero no he encontrado como, alguno de ustedes podría apoyarme
Hello, can someone help me, I need to get a list of all the computers in my domain and that each computer shows the version of Bios that it has installed but I have not found how, could any of you help meTry this:
$computers = (Get-ADComputer -Filter 'enabled -eq "true"').Name$results = Invoke-Command $computers -ScriptBlock {Get-WmiObject -Class Win32_BIOS | select SMBIOSBIOSVersion}
$results | Select-Object PSComputerName, SMBIOSBIOSVersion