Broadcast protocols NetBIOS over TCP/IP, LLMNR, and mDNS (Multicast DNS) are used to resolve names in Windows networks where there is no (unavailable) DNS server (typically, these are home or SOHO networks). These protocols are usually not needed in corporate networks with DNS servers. In addition, these broadcast protocols are not secure and can easily be used by attackers to implement spoofing, relay, and MITM attacks, which can intercept user credentials on the local subnet (including NTLM hashes). Let’s look at how to disable the LLMNR, NetBIOS, and mDNS protocols on a Windows network, either manually or via GPO.
Non-DNS Resolution Protocols in Windows: LLMNR, NetBIOS, mDNS
DNS is the preferred name resolution protocol on Windows networks. If there are no DNS servers available on the network, alternative resolution protocols are used in the following order:
- MulticastDNS (mDNS)
- Link-Local Multicast Name Resolution (LLMNR)
- NetBIOS (NBNS)
LLMNR (UDP/5355, Link-Local Multicast Name Resolution) protocol is used in all Windows versions starting from Vista, allows IPv6 and IPv4 clients to resolve the names of neighboring computers without using the DNS server due to broadcast requests in the local L2 network segment. This protocol is automatically used if DNS is unavailable (in Windows workgroups this protocol is used for Network Discovery).
NetBIOS over TCP/IP or NBT-NS (UDP/137,138, TCP/139) is a broadcast protocol that predates LLMNR and is used to publish and discover resources on the local network. NetBIOS over TCP/IP is enabled by default on all Windows interfaces.
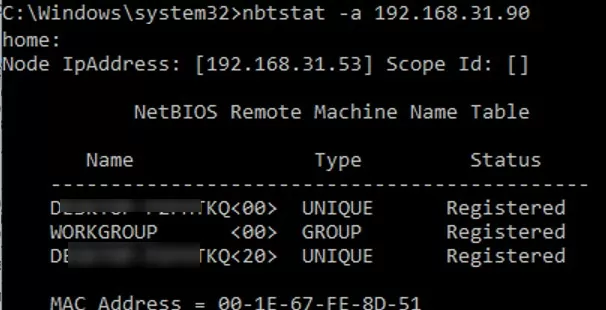
On Windows, you can view NetBIOS statistics and current TCP/IP connections through NBT using the nbtstat command. To get the computer name by its IP address:
nbtstat -A 192.168.131.190
The nbtstat tool found a computer on the local network using NetBIOS and returned the name of that computer. You can list all of the entries about the neighboring computers on the same local network from the NetBIOS cache:
nbtstat -c
The Multicast DNS (mDNS) network protocol is available starting with Windows 10 version 1703 and Windows Server 2019. It enables the resolution of host names to IP addresses on small local networks without using a central DNS server. Name uniqueness within the LAN is ensured by the addition of the .local suffix. mDNS was supposed to completely replace the legacy NetBIOS and LLMNR protocols. Multicast UDP packets on port 5353 are used for name resolution. In addition, mDNS is widely used to automatically discover network printers, screens, and other services on a LAN.
When DNS is unavailable, the NetBIOS, LLMNR, and mDNS protocols allow workgroup computers to find devices on the LAN by name. These protocols can be disabled in a corporate domain environment.
Disable LLMNR Protocol on Windows via GPO
In the Active Directory environment, Group Policy can be used to disable LLMNR broadcasts on domain computers and servers.
- Open the
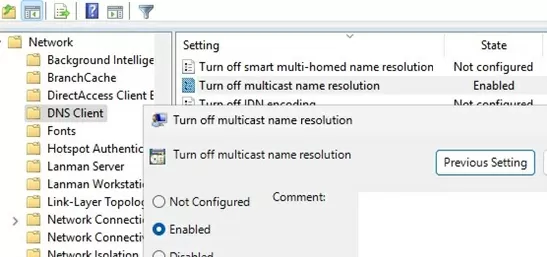
gpmc.msc, create a new GPO or edit an existing one that is applied to all workstations and servers - Go to Computer Configuration -> Administrative Templates -> Network -> DNS Client;
- Enable the Turn off multicast name resolution and Turn off smart multi-homed name resolution policies
- Wait for the GPO settings to be updated on the clients, or manually update them using the command:
gpupdate /force
Or, disable the LLMNR protocol in Windows by creating these registry options using PowerShell:
New-Item "HKLM:\SOFTWARE\Policies\Microsoft\Windows NT" -Name DNSClient -Force
New-ItemProperty "HKLM:\SOFTWARE\Policies\Microsoft\Windows NT\DNSClient" -Name EnableMultiCast -Value 0 -PropertyType DWORD -Force
New-ItemProperty "HKLM:\SOFTWARE\Policies\Microsoft\Windows NT\DNSClient" -Name DisableSmartNameResolution -Value 1 -PropertyType DWORD -Force
Disabling NetBIOS over TCP/IP on Windows
You can manually disable the NetBIOS protocol in the network adapter settings:
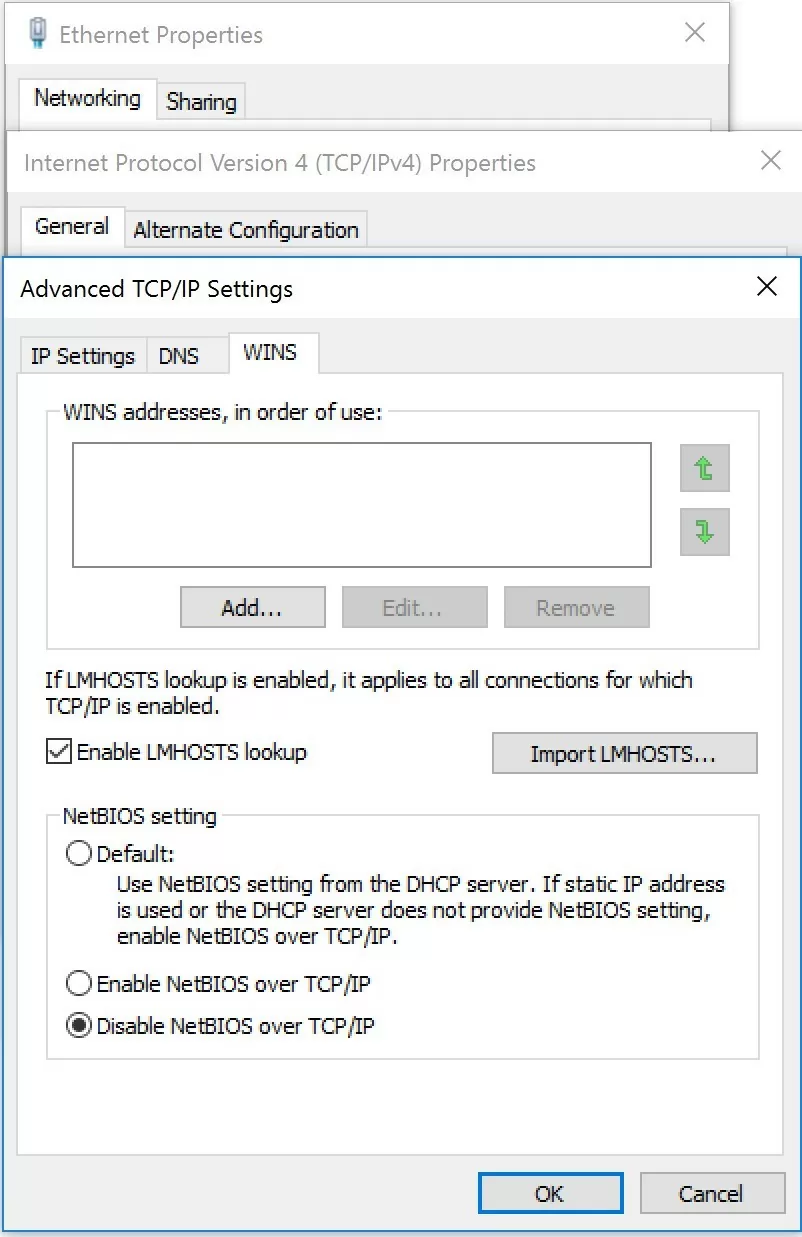
- Open network connection properties in the
ncpa.cplapplet - Select TCP/IPv4 and open its properties
- Click Advanced, then go to the WINS tab and select Disable NetBIOS over TCP
- Save the changes.
If you have multiple NICs (or VLAN interfaces), be sure to disable NetBIOS in the properties of each of them.
Check the NetBIOS over TCP/IP status for network adapters from the Windows command prompt:
ipconfig /all |find "NetBIOS"
NetBIOS over Tcpip . . . . . : Disabled
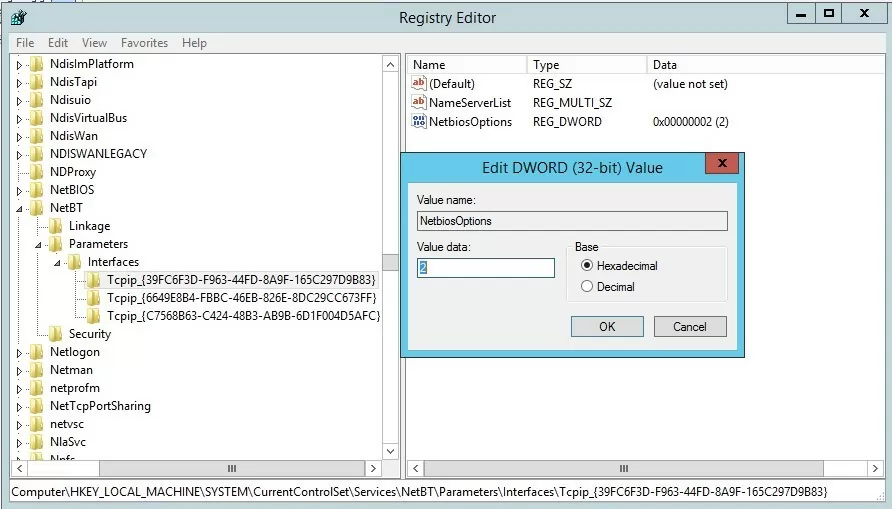
You can disable NetBIOS for the specific network adapter through the registry as well. Each network adapter has a separate registry key under HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NetBT\Parameters\Interfaces containing its TCPIP_GUID.
To disable NetBIOS for a specific network adapter, go to its registry key and change the value of the NetbiosOptions parameter to 2 (it is 0 by default).
For domain clients that obtain their IP addresses from a Windows Server DHCP, you can use a separate DHCP option to disable NetBIOS.
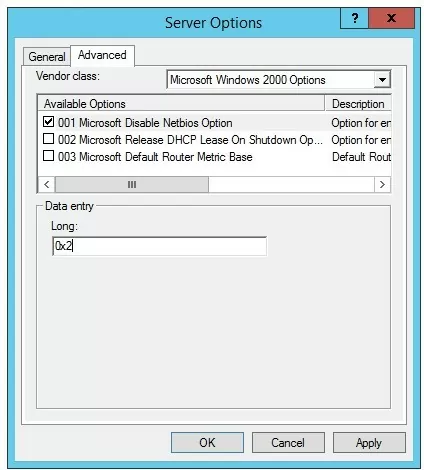
- Run the
dhcpmgmt.mscconsole, connect to the DHCP server, and select Scope Option (or Server Options); - Go to the Advanced tab and select Microsoft Windows 2000 Options in the Vendor class dropdown list;
- Enable the 001 Microsoft Disable Netbios Option and change its value to 0x2.
How to Disable NetBIOS Over TCP/IP via GPO
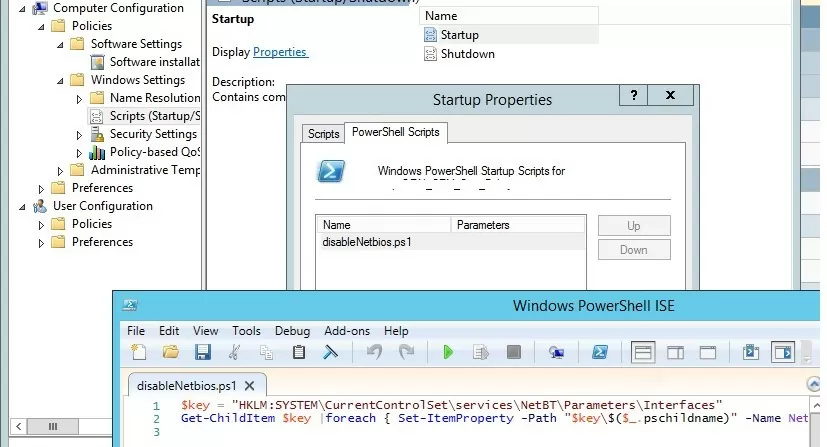
There is no separate GPO option to disable NetBIOS over TCP/IP for all network adapters in the Group Policy Editor or in the latest version of ADMX GPO administrative templates for Windows. To completely disable NetBIOS for all network adapters, use the following PowerShell logon script:
$regkey = "HKLM:SYSTEM\CurrentControlSet\services\NetBT\Parameters\Interfaces"
Get-ChildItem $regkey |foreach { Set-ItemProperty -Path "$regkey\$($_.pschildname)" -Name NetbiosOptions -Value 2 -Verbose}
Or use a PowerShell oneliner with a WMI query:
Get-WmiObject -Class Win32_NetworkAdapterConfiguration | % {$_.SetTcpipNetbios(2)}
Save this code to disableNetbios.ps1 file, copy it to your GPO directory and run on clients via Computer Configuration -> Policies -> Windows Settings -> Scripts -> Startup- > PowerShell Scripts.
Next, open a command prompt and verify that NetBIOS is disabled for network adapters (except for tunneling interfaces):
wmic nicconfig get caption,index,TcpipNetbiosOptions
Disable Multicast DNS (mDNS) in Windows
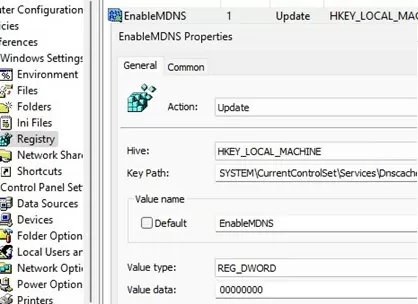
To disable the mDNS protocol on a Windows device, create the EnableMDNS parameter with value 0 under the HKLM\SYSTEM\CurrentControlSet\Services\Dnscache\Parameters registry key.
The command can be used to set this registry option :
REG ADD "HKLM\SYSTEM\CurrentControlSet\Services\Dnscache\Parameters" /v " EnableMDNS" /t REG_DWORD /d "0" /f
Or, deploy the registry parameter via Group Policy Preferences (Computer Configuration > Preferences > Windows Settings > Registry)
- Action: Update
- Hive: HKEY_LOCAL_MACHINE
- Key Path: SYSTEM\CurrentControlSet\Services\Dnscache\Parameters
- Value name: EnableMDNS
- Value type: DWORD
- Value data: 0
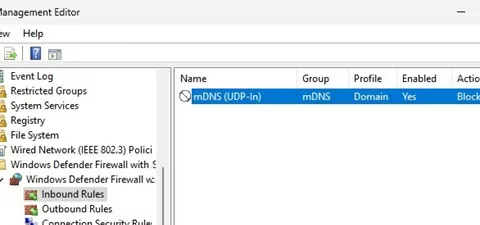
You can also use a GPO to deploy a Windows Defender firewall rule that blocks inbound mDNS traffic on domain computers. Or, disable the mDNS (UDP-In) rule for the domain profile only. This allows users’ laptops to discover nearby devices on the network via mDNS when working outside the domain (office).
Run the following commands to verify that the NetBIOS, LLMNR, and mDNS protocols are disabled on a computer:
netstat -nao | FIND /i ":137 "
netstat -nao | FIND /i ":5353 "
netstat -nao | FIND /i ":5355 "
If these name resolution protocols are disabled, the commands should not return any open ports.