Every Windows system administrator should be able to use not only graphical AD snap-ins (usually it is ADUC, Active Directory Users and Computers), but also PowerShell cmdlets to perform everyday Active Directory administration tasks. Most commonly, the Active Directory module for Windows PowerShell is used for domain and object management tasks (users, computers, groups). In this article, we will look at how to install theRSAT-AD-PowerShell module on Windows, discover its basic features, and popular cmdlets that are useful to manage and interact with AD.
How to Install the Active Directory PowerShell Module on Windows 10 and 11
You can install the RSAT-AD PowerShell module not only on servers but also on workstations. This module is included in the RSAT (Remote Server Administration Tools) package for Windows.
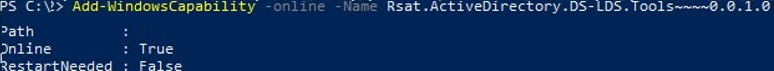
In current builds of Windows 11 and Windows 10, the RSAT components are installed online as Features on Demand. You can install the module by using the command:
Add-WindowsCapability -online -Name Rsat.ActiveDirectory.DS-LDS.Tools~~~~0.0.1.0
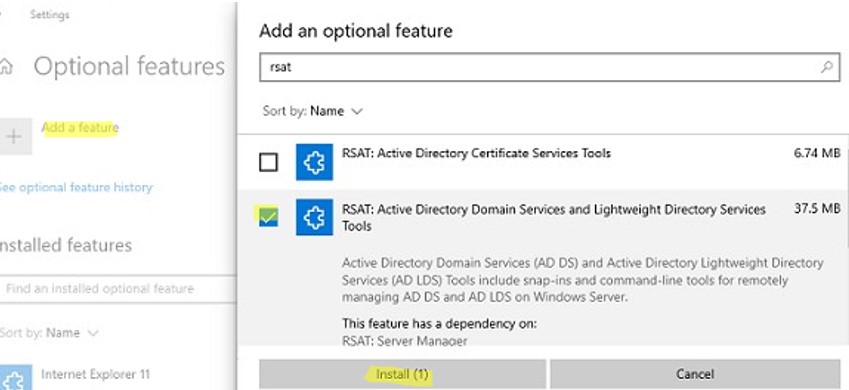
Or through via the Settings -> Apps -> Optional features -> Add a feature -> RSAT: Active Directory Domain Services and Lightweight Directory Services Tools.
You must first install the WindowsCompatibility module to use AD cmdlets in PowerShell Core 6.x, 7.x:
Install-Module -Name WindowsCompatibility
Then load the module into your session:
Import-Module -Name WindowsCompatibility
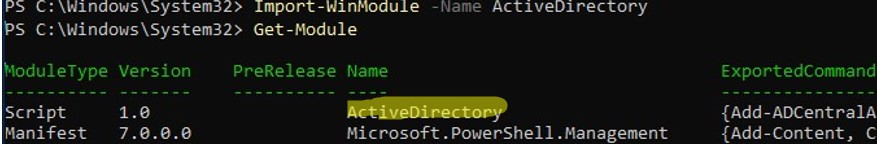
Import-WinModule -Name ActiveDirectory
Now you can use AD cmdlets in your PowerShell Core 7.x scripts.
Installing the RSAT-AD-PowerShell Module on Windows Server
On Windows Server, you can install the Active Directory Module for Windows PowerShell from the Server Manager graphical console or by using PowerShell.
You can check that the Active Directory module is installed with the command:
Get-WindowsFeature -Name "RSAT-AD-PowerShell"
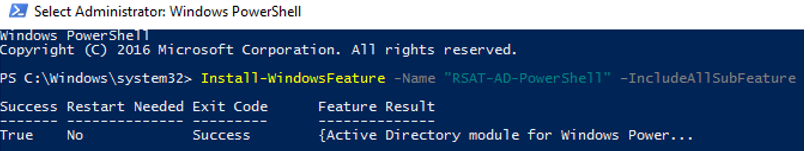
If the module is missing, install it:
Install-WindowsFeature -Name "RSAT-AD-PowerShell" –IncludeAllSubFeature
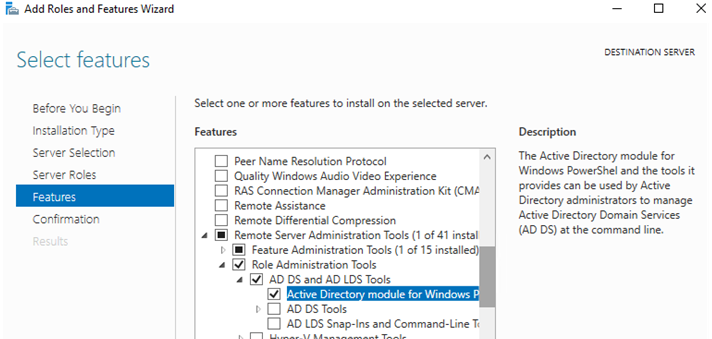
To install the module through the Server Manager, go to Add Roles and Features -> Features -> Remote Server Administration Tools -> Role Administration Tools -> AD DS and AD LDS Tools -> enable the Active Directory module for Windows PowerShell.
You do not need to use a local domain controller session to manage Active Directory by using the RSAT-AD PowerShell module. This module can be installed on any member server or workstation. On AD domain controllers, the module is automatically installed when the Active Directory Domain Services (AD DS) role is deployed (when the server is promoted to a DC).
The module interacts with AD through the Active Directory Web Service that must be running on your domain controller and available to clients on a TCP port 9389. Use the Test-NetConnection cmdlet to verify that this port is not blocked by a firewall on the DC:
Test-NetConnection MUN-DC1 -port 9389
Active Directory Administration with PowerShell
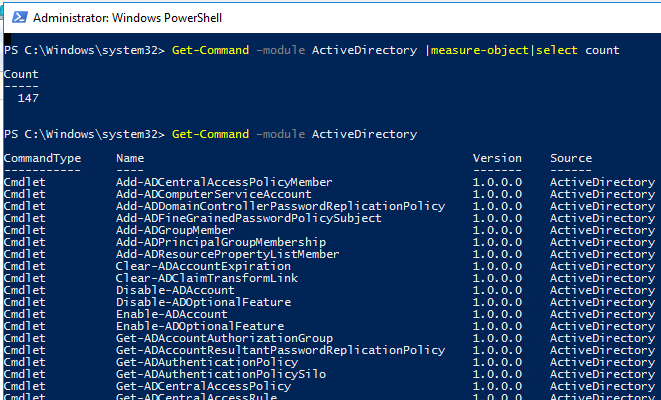
The Active Directory module for Windows PowerShell has a large number of cmdlets for interacting with AD. There are 147 AD PowerShell cmdlets available in the current version of the module for Windows Server 2022/Windows 11.
Check that the module is installed on the computer:
Get-Module -Name ActiveDirectory –ListAvailable
Before you can use the Active Directory module cmdlets, you must import it into your PowerShell session (starting from Windows Server 2012 R2/ Windows 8.1 the module is imported automatically).
Import-Module ActiveDirectory
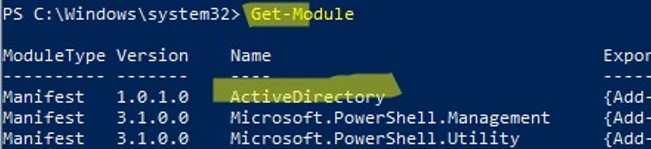
Make sure that the AD module is loaded in your PowerShell session:
Get-Module
You can display a complete list of available Active Directory cmdlets:
Get-Command –module ActiveDirectory
The total number of cmdlets in the AD module:
Get-Command –module ActiveDirectory |measure-object|select count
Most of the RSAT-AD PowerShell module cmdlets begin with the Get-, Set- or New- prefixes.
- Get– class cmdlets are used to get different information from Active Directory (
Get-ADUser— user properties,Get-ADComputer– computer settings,Get-ADGroupMember— group membership, etc.). You do not need to be a domain administrator to use these cmdlets. Any domain user can run PowerShell commands to get the values of the AD object attributes (except confidential ones, like in the example with LAPS); - Set- class cmdlets are used to set (change) object properties in Active Directory. For example, you can change user properties (Set-ADUser), computer settings (Set-ADComputer), etc. To perform these actions, your account must have write permissions on the objects you want to modify (see the article How to Delegate Administrator Privileges in Active Directory);
- Commands that start with New- allow you to create AD objects (create a user —
New-ADUser, create a group —New-ADGroup, create an Organizational Unit —New-ADOrganizationalUnit); - Cmdlets starting with Add-: add a user to a group (
Add-ADGroupMember), add a Fine-Grained Password Policy (Add-ADFineGrainedPasswordPolicySubject); - Remove- cmdlets are used to delete AD objects
Remove-ADGroup,Remove-ADComputer,Remove-ADUser).
There are specific PowerShell cmdlets that you can use to manage only certain AD components:
Enable-ADOptionalFeature– enable optional AD features (for example, AD Recycle Bin to restore deleted objects);Install-ADServiceAccount– configure managed service account (MSA, gMSA);Search-ADAccount– allows you to find disabled, inactive, locked user and computer accounts in Active Directory;Enable-ADAccount/Disable-ADAccount/Unlock-ADAccount– enable/disable/unlock an account.
By default, the PowerShell cmdlets connect to the nearest domain controller in your environment (LOGONSERVER). With the -Server parameter, you can connect to ADDS on a different domain controller or in a different domain (you can display a list of DCs in another domain using the nltest /dclist:newad.com command).
The -Server parameter is available for nearly all of the module cmdlets. For example
Get-ADuser j.smith -Server mun-dc1.woshub.com
You can also use the -Credential parameter to specify alternative Active Directory user credentials.
$creds = Get-Credential
Get-ADUser -Filter * -Credential $creds
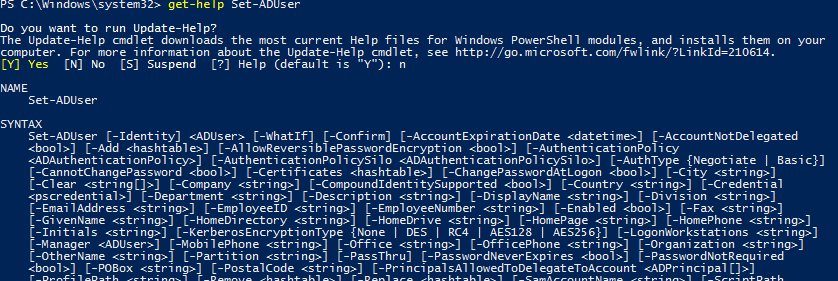
Here is how you can get help on any cmdlet
get-help Set-ADUser
You can display the examples of using Active Directory cmdlets as follows:
(get-help New-ADComputer).examples
Importing Active Directory PowerShell Module from a Remote Computer
It is not necessary to install the AD PowerShell module on all computers. An administrator can remotely import this module from a domain controller (domain administrator privileges are required) or from any other computer.
PowerShell Remoting is used to connect to a remote computer. This requires that Windows Remote Management (WinRM) is enabled and configured on the remote host.
Create a new session with the remote computer that has the AD PowerShell module installed:
$psSess = New-PSSession -ComputerName DC_or_Comp_with_ADPosh
Import the ActiveDirectory module from the remote computer into your local PS session:
Import-Module -PSsession $psSess -Name ActiveDirectory
Now you can run any commands from the Active Directory module on your computer as if the module was installed locally. However, they will be executed on a remote host.
notepad $profile.CurrentUserAllHosts to open your PS profile file.You can end a remote session with the command :
Remove-PSSession -Session $psSess
This method of importing the AD module through PowerShell implicit remoting allows you to use PowerShell cmdlets from Linux and MacOS hosts that cannot install a local copy of the module.
You can also >use the Active Directory Module for PowerShell without installing RSAT. To do this, simply copy some files from a computer where the RSAT-AD PowerShell module is installed:
- Directory
C:\Windows\System32\WindowsPowerShell\v1.0\Modules - File
ActiveDirectory.Management.dll - File
ActiveDirectory.Management.resources.dll
Then you need to import the module into your current session:
Import-Module C:\PS\ADmodule\Microsoft.ActiveDirectory.Management.dll
Import-Module C:\PS\ADmodule\Microsoft.ActiveDirectory.Management.resources.dll
After that, you can use all of the AD module cmdlets without installing RSAT.
Common PowerShell Commands for Active Directory
Let’s take a look at some typical administrative tasks that can be performed using the Active Directory for PowerShell cmdlets.
New-ADUser: Creating AD Users
To create a new AD user, you can use the New-ADUser cmdlet. You can create a user with the following command:
New-ADUser -Name "Mila Beck" -GivenName "Mila" -Surname "Beck" -SamAccountName "mbeck" -UserPrincipalName "[email protected]" -Path "OU=Users,OU=Berlin,OU=DE,DC=woshub,DC=com" -AccountPassword(Read-Host -AsSecureString "Input User Password") -Enabled $true
For detailed info about the New-ADUser cmdlet (including an example on how to create user domain accounts in bulk), see this article.
Get-ADComputer: Getting Computer Object Properties
To get the properties of computer objects in a particular OU (the computer name and the last logon date), use the Get-ADComputer cmdlet:
Get-ADComputer -SearchBase ‘OU=CA,OU=USA,DC=woshub,DC=com’ -Filter * -Properties * | FT Name, LastLogonDate -Autosize
Add-ADGroupMember: Add Active Directory Users to Group
To add users to an existing security group in an AD domain, run this command:
Add-AdGroupMember -Identity LondonSales -Members e.braun, l.wolf
Display the list of users in the AD group and export it to a CSV file:
Get-ADGroupMember LondonSales -recursive| ft samaccountname| Out-File c:\ps\export_ad_users.csv
Set-ADAccountPassword: Reset a User Password in AD
In order to reset a user’s password in AD with PowerShell:
Set-ADAccountPassword m.lorenz -Reset -NewPassword (ConvertTo-SecureString -AsPlainText “Ne8Pa$$0rd1” -Force -Verbose) –PassThru
How to Unlock, Enable, and Disable Active Directory Accounts?
To disable the AD user account:
Disable-ADAccount m.lorenz
To enable an account:
Enable-ADAccount m.lorenz
Unlock an account after it has been locked by a domain password policy:
Unlock-ADAccount m.lorenz
Search-ADAccount: How to Find Inactive and Disabled AD Objects?
To find and disable all computers in the AD domain that have not logged on for more than 90 days, use the Search-ADAccount cmdlet:
$timespan = New-Timespan –Days 90
Search-ADAccount -AccountInactive -ComputersOnly –TimeSpan $timespan | Disable-ADAccount
New-ADOrganizationalUnit: Create an Organizational Unit in AD
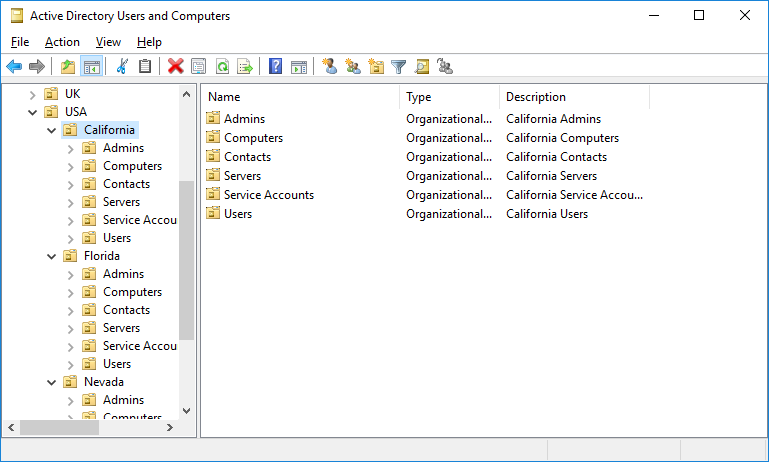
To quickly create a typical Organizational Unit structure in AD, you can use a PowerShell script. Suppose you want to create multiple OUs with states as their names and create typical object containers. It is quite time-consuming to create this AD structure manually through the graphical ADUC snap-in. AD module for PowerShell allows solving this task in seconds (except the time to write the script):
$fqdn = Get-ADDomain
$fulldomain = $fqdn.DNSRoot
$domain = $fulldomain.split(".")
$Dom = $domain[0]
$Ext = $domain[1]
$Sites = ("Nevada","Texas","California","Florida")
$Services = ("Users","Admins","Computers","Servers","Contacts","Service Accounts")
$FirstOU ="USA"
New-ADOrganizationalUnit -Name $FirstOU -Description $FirstOU -Path "DC=$Dom,DC=$EXT" -ProtectedFromAccidentalDeletion $false
foreach ($S in $Sites)
{
New-ADOrganizationalUnit -Name $S -Description "$S" -Path "OU=$FirstOU,DC=$Dom,DC=$EXT" -ProtectedFromAccidentalDeletion $false
foreach ($Serv in $Services)
{
New-ADOrganizationalUnit -Name $Serv -Description "$S $Serv" -Path "OU=$S,OU=$FirstOU,DC=$Dom,DC=$EXT" -ProtectedFromAccidentalDeletion $false
}
}
After you run the script, you will see the following OU structure in the Active Directory.
To move objects between AD containers, you can use the Move-ADObject cmdlet:
$TargetOU = "OU=Sales,OU=Computers,DC=woshub,DC=com"
Get-ADComputer -Filter 'Name -like "SalesPC*"' | Move-ADObject -TargetPath $TargetOU
Get-ADReplicationFailure: Check Active Directory Replication
You can use the Get-ADReplicationFailure cmdlet to check the status of replication between AD domain controllers:
Get-ADReplicationFailure -Target NY-DC01,NY-DC02
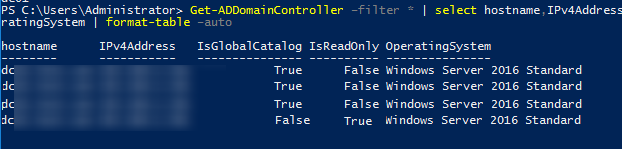
To get information about all DCs in the domain, use the Get-AdDomainController cmdlet:
Get-ADDomainController –filter * | select hostname,IPv4Address,IsGlobalCatalog,IsReadOnly,OperatingSystem | format-table –auto
In this article, we looked at how to install and use the Active Directory PowerShell module for AD domain administration. I hope this article will encourage you to further explore this module and start automating most of your AD management tasks.
1 comment
BRO
THE F**ING LINE:
Add-WindowsCapability –online –Name “Rsat.ActiveDirectory.DS-LDS.Tools~~~~0.0.1.0”
HAS DIFFERENT GOD DAMN UNICODE CHARACTERS IN IT
THE “-” IN THAT LINE IS NOT A HYPHEN.
🙁