The version of Active Directory in Windows Server 2016 introduces an interesting feature that allows you to temporarily add a user to an AD security group. This feature is called Temporary Group Membership (Time Based). This feature can be used when you need to temporarily grant a user some authority based on AD security group membership. After the specified time has elapsed, the user will be automatically removed from the security group (without administrator intervention).
To use the Temporary Group Membership, you need to enable the Privileged Access Management Feature in your Active Directory forest. Like with AD Recycle Bin (which allows you to recover deleted objects), you cannot disable PAM after it has been enabled.
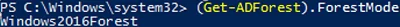
Make sure your AD forest is running at Windows Server 2016 forest function level (or higher):
(Get-ADForest).ForestMode
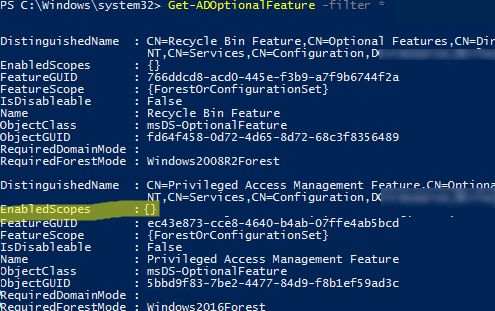
Check if the Privileged Access Management feature is enabled in the current forest using the command from the AD PowerShell module:
Get-ADOptionalFeature -filter "name -eq 'privileged access management feature'"
We need the value of EnableScopes parameter. It is empty in our example. It means that the Privileged Access Management Feature is not enabled for this forest.
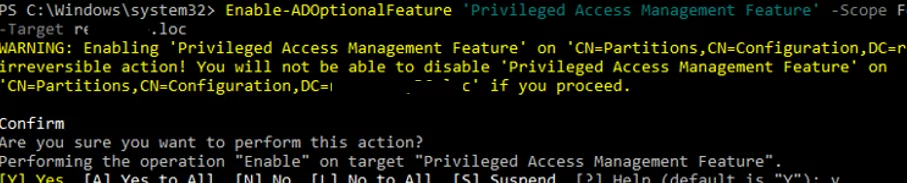
To activate it, use Enable-ADOptionalFeature command, and specify your forest name as one of the arguments:
Enable-ADOptionalFeature 'Privileged Access Management Feature' -Scope ForestOrConfigurationSet -Target contoso.com
Enable-ADOptionalFeature: The SMO role ownership could not be verified because its directory partition has not replicated successfully with at least one replication partner” appears when running the command, check the status of the domain controllers and AD replication, and the availability of FSMO role owners. Manually force AD replication.Run the command Get-ADOptionalFeature -filter "name -eq 'privileged access management feature'" | select EnabledScopes and check that the EnableScopes field is not empty.
dsa.msc) is not supported.After PAM has been enabled, you can try to add a user to an AD group using a special argument MemberTimeToLive of Add-ADGroupMember cmdlet. It is convenient to set the time interval (TTL) using the New-TimeSpan cmdlet. Let’s say you want to add the user test1 to the Domain Admins group for 15 minutes:
$ttl = New-TimeSpan -Minutes 5
Add-ADGroupMember -Identity "Domain Admins" -Members test1 -MemberTimeToLive $ttl
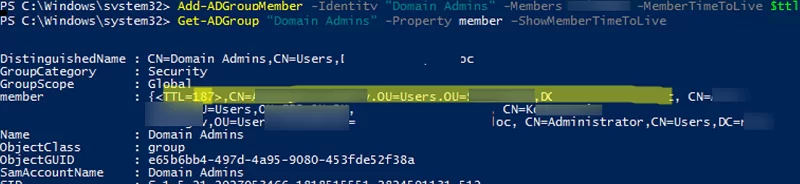
You can check how much time a user will be a group member using the Get-ADGroup cmdlet:
Get-ADGroup 'Domain Admins' -Property member –ShowMemberTimeToLive
In the command results, you can see an entry like <TTL=187,CN=test1,CN=Users,DC=woshub,DC=loc> for the group members. The TTL value is displayed in seconds. This means that this user has been added to the Domain Admins group temporarily. After 187 seconds, he will be automatically removed from the group
The user Kerberos ticket also expires. This is implemented because KDC issues a ticket with the lifetime equal to the least of TTL value for the user having a temporary membership in the AD groups.
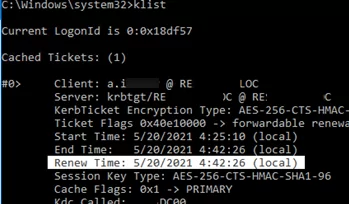
You can check the next Kerberos ticket renewal time with the command:
klist
The time of the next renewal of the TGT ticket is displayed in the Renew Time parameter.
Also in AD (with Windows2003Fores forest functional level or newer), you can create temporary AD groups. For such groups, the dynamicObject class is used. Automatic deletion of such groups is performed by the Active Directory Garbage Collection process.
For example, to create a temporary group that will be automatically deleted after a month (2592000 = 31 * 24 * 60 * 60), use the following PowerShell script:
$OU = [adsi]"LDAP://OU=Groups,OU=Munich,OU=DE,DC=woshub,DC=loc"
$Group = $OU.Create("group","cn=MUN-FS01_Public_tmp")
$Group.PutEx(2,"objectClass",@("dynamicObject","group"))
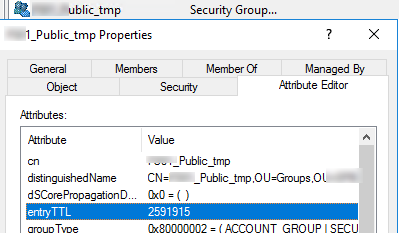
$Group.Put("entryTTL","2678400")
$Group.SetInfo()
Open the group attributes in the ADUC console. Pay attention to the entryTTL attribute. It indicates in how many seconds this AD group will be removed.
Earlier, to implement a temporary AD group membership, you had to use dynamic objects, different scripts and scheduled tasks, or quite complex systems (Microsoft Forefront Identity Manager, etc.). Now, in Windows Server 2016/2019, this handy feature is available out of the box.
9 comments
[…] https://woshub.com/temporary-membership-in-active-directory-groups/ […]
[…] https://woshub.com/temporary-membership-in-active-directory-groups/ […]
Great Article! Thank you very much.
But I have a question. You say: “It is not recommended to use temporary group membership to provide temporary access to privileged domain groups (Enterprise admins, Domain admins, etc.).”
Why?
The user can grant himself permanent privileged permissions in the AD domain during the temporary membership.
Thank your for the answer! So I understand that the reasoning behind this sentence is purely organizational. There is no technical reason not to do it, it won’t break anything or cause some kind of incompatibility. Correct?
Organizational, it’s in the nature of the matter, I guess. Like if you give the key to your house to a cleaner, he can make a copy of the key. But at some point you’ll have to trust someone with some means of access, otherwise you’ll have to clean yourself. At least in digital systems like AD we have the big advantage that we can address this issue by monitoring the members of security-critical groups and report any new that should no be there.
You are absolutely right!
Hello… I have the following problem: when I add a user to an AD group with the script, add for a limited time as I define in Active Directory, this is synchronized with Azure AD, but when the user is removed from the AD group, only is reflected in the Active Directory.
What can this be?
I have the same problem. After TTL expires, user is removed from on prem group, but not from azure group.
Can someone help?
Azure AD Connect sync does not currently support syncing the TTL-based membership expiration from on-prem AD to the Entra ID group.
So you should use some workaround, such as a custom script that detects TTL expirations on-premises and explicitly removes users from the corresponding EntraID groups.