The Microsoft Defender Firewall is built into all modern versions of Windows and Windows Server and allows you to configure rules for filtering incoming and/or outgoing network traffic on your computer. Windows Firewall rules can be configured locally on the user’s computer (using the wf.msc console, the netsh command, or the built-in NetSecurity PowerShell module). On Windows computers joined to an Active Directory domain, you can centrally manage Microsoft Defender Firewall rules and settings using Group Policies.
In enterprise networks, the port filtering rules are usually set at the level of routers, L3 switches, or dedicated firewall devices. However, nothing prevents you from deploying your Windows Firewall network access rules to workstations or Windows servers.
Enable Microsoft Defender Firewall via GPO
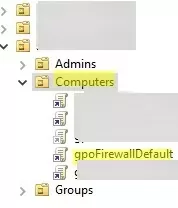
Open the domain Group Policy Management console (gpmc.msc), create a new GPO object (policy) with the name gpoFirewallDefault, and switch to Edit mode.
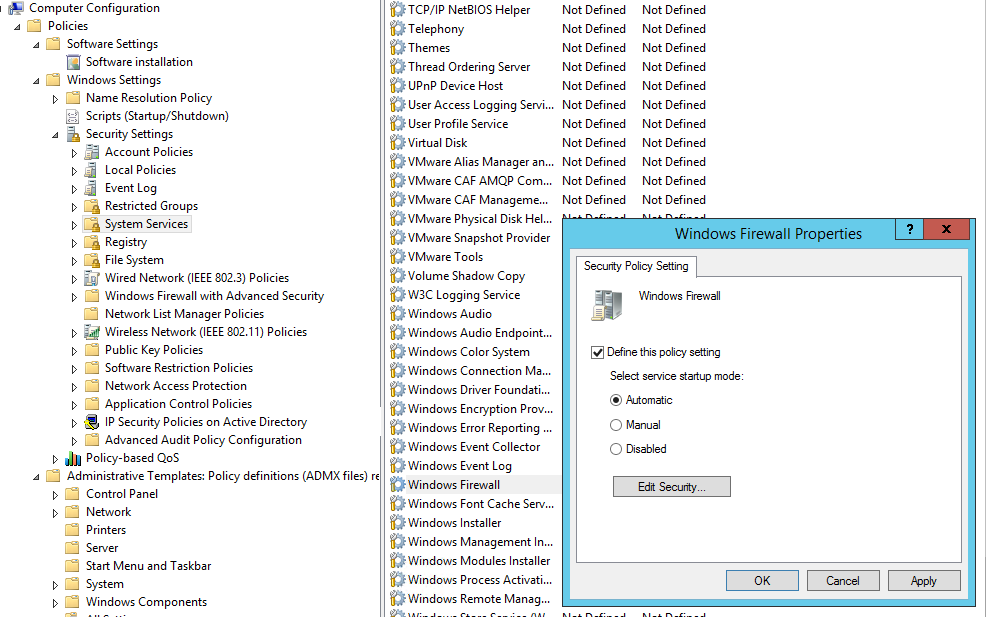
In order to prevent users (even having local admin permissions) to stop the firewall service, it is recommended to configure the automatic startup of the Windows Firewall using GPO. To do it, go to Computer Configuration- > Windows Settings -> Security Settings -> System Services. Find Windows Firewall in the list of services and change the startup type to automatic (Define this policy setting -> Service startup mode Automatic). Make sure that your users don’t have the permission to stop the service.
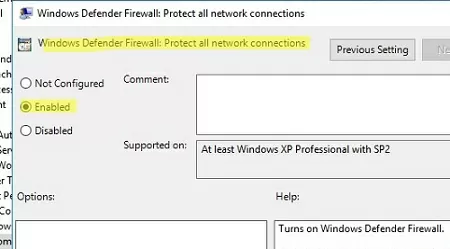
Then go to Computer Configuration -> Policies -> Administrative Templates -> Network -> Network Connections -> Windows Defender -> Firewall -> Domain Profile and enable the policy Windows Defender Firewall: Protect all network connections.
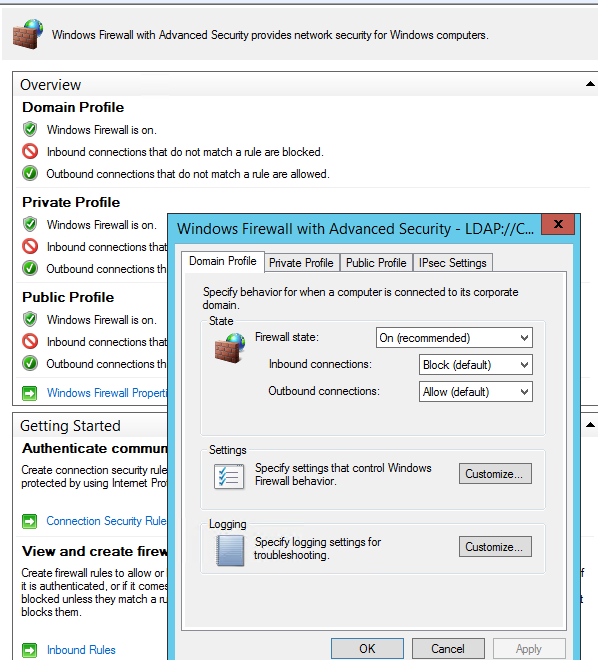
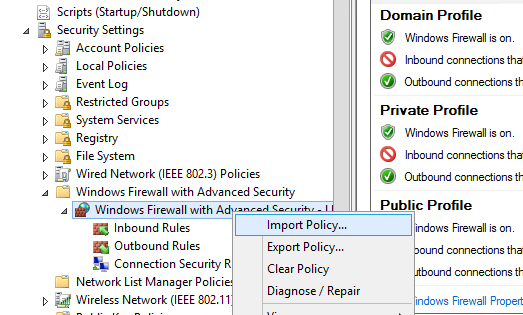
Go to the Computer Configuration -> Windows Settings -> Security Settings section in the GPO console. Right-click Windows Firewall with Advanced Security and open the properties.
Change the Firewall state to On (recommended) in all three tabs: Domain Profile, Private Profile, and Public Profile (What are network profiles (locations) in Windows?). Depending on the security policies in your company, you can specify that all inbound connections are blocked by default (Inbound connections -> Block), and outbound connections are allowed (Outbound connections -> Allow). Save the changes.
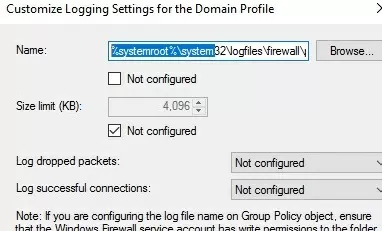
You can debug your Windows Defender Firewall rules on clients’ computers by enabling logging in %systemroot%\system32\logfiles\firewall\pfirewall.log. By default, network connection logging is disabled in Windows. You can log only rejected packets (Log dropped packets) or packets that were allowed by firewall rules (Log successful connections).
How to Create Windows Firewall Rule with GPO?
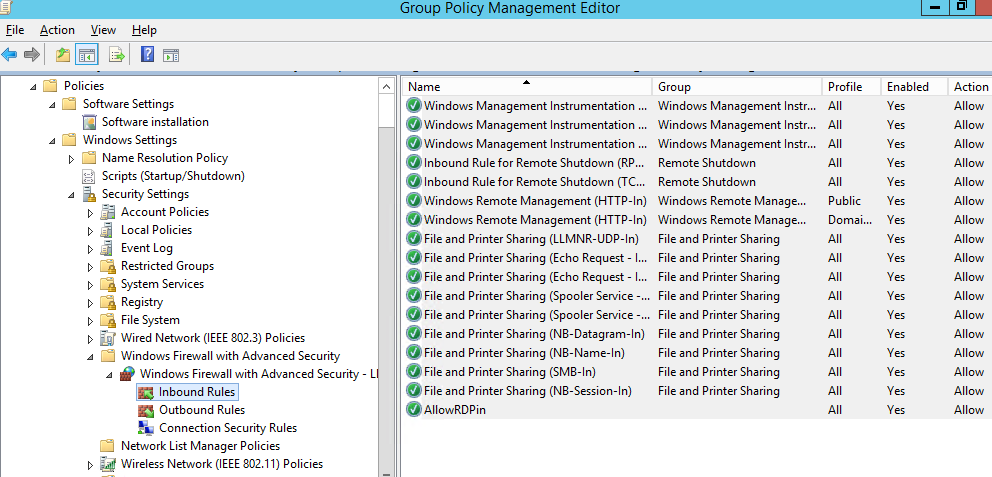
Now let’s look at how to create Microsoft Defender firewall rules via Group Policy. To configure your rules, go to Computer Configuration -> Windows Settings -> Security Settings -> Windows Firewall with Advanced Security.
The following sections are available in Firewall GPO:
- Inbound rules
- Outbound rules
- Connection security rules
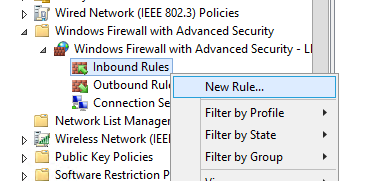
Let’s try to create an allowing inbound firewall rule. For example, we want to allow the incoming RDP connection on Windows (the default RDP port is TCP 3389). Right-click the Inbound Rules section and select New Rule. The New Firewall Rule Wizard starts.
The firewall rule wizard has an interface similar to that of the local Windows Firewall on the user’s desktop computer.
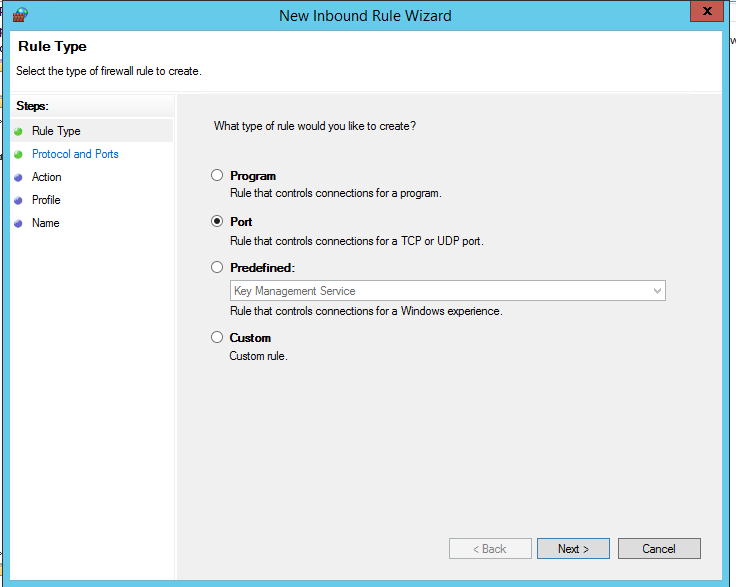
Select the rule type. You can allow access to:
- Program – you can select a program executable (.exe);
- Port – you can select a TCP/UDP port or a port range;
- Predefined – select one of the standard Windows rules, which already contain access rules (both executable files and ports are described) to typical services (e. g., AD, HTTP(s), DFS, BranchCache, Remote restart, SNMP, KMS, WinRM, etc.);
- Custom – here you can specify a program, a protocol (protocols other than TCP or UDP, like ICMP, GRE, L2TP, IGMP, etc.), client IP addresses, or an entire IP network (subnet).
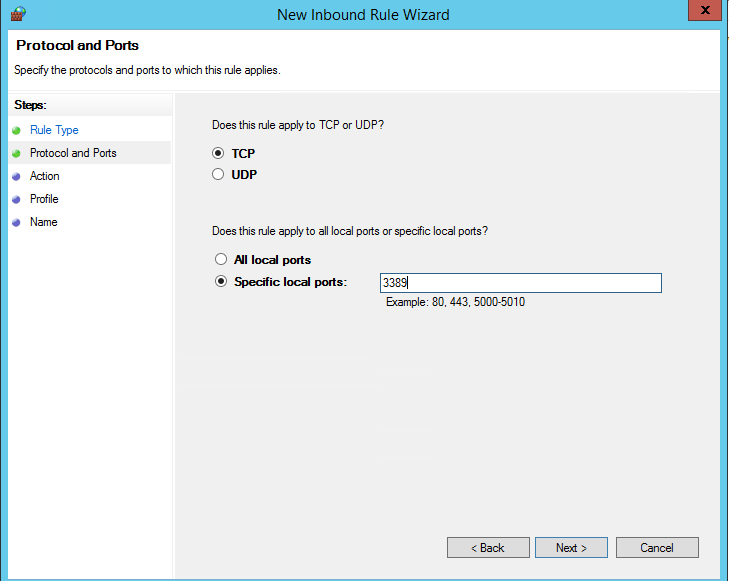
In our case, we’ll select the Port rule. Let’s specify TCP as the protocol, and 3389 as the local port number.
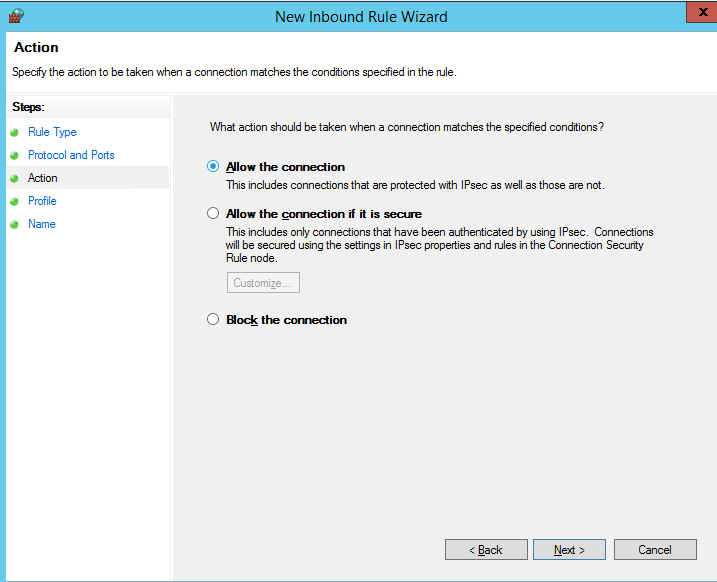
Then you must select what to do with such a network connection: Allow the connection, Allow the connection if it is secure, or Block the connection.
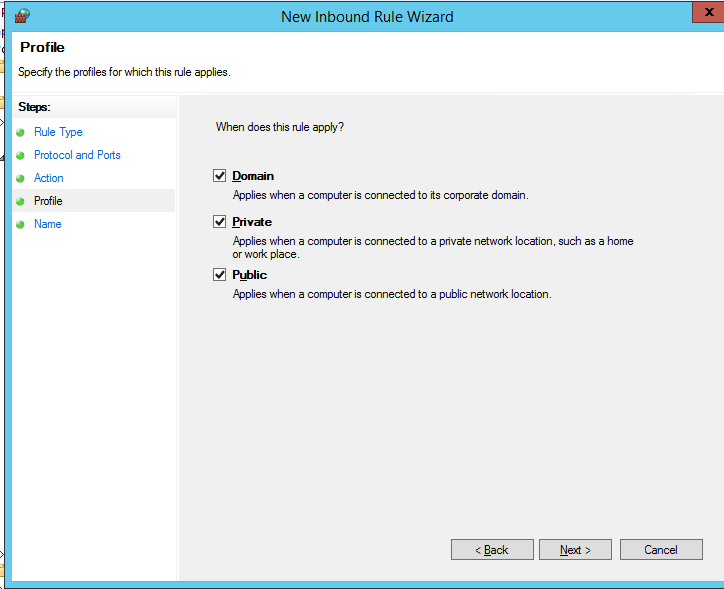
Then select the network profiles to apply the firewall rule. You can leave all profiles enabled (Domain, Private and Public).
In the last step, specify the name and description of the rule. Click Finish, and it will appear in the list of firewall rules.
In the same way, you can configure other inbound firewall rules to apply to your Windows clients. You can create rules for both inbound and outbound traffic.
Above, we looked at how to use the graphical wizard to create Windows Defender Firewall rules. You can also create a list of rules in plain text form and quickly add a large number of exceptions to Defender Firewall GPO.
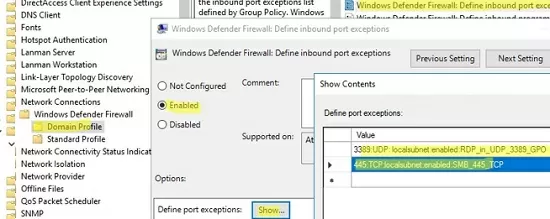
Go to Computer Configuration -> Policies -> Administrative Templates -> Network -> Network Connections -> Windows Defender Profile -> Domain Profile and open the Windows Defender Firewall: Define inbound port exceptions policy. Here you can create a list of firewall rules with simple text strings.
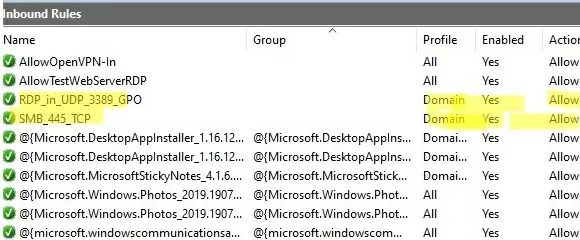
Below is the list of inbound firewall rules that I want to add to the Group Policy:
3389:UDP:localsubnet:enabled:In_RDP_UDP_3389 445:TCP:localsubnet:enabled:In_SMB_TCP_443 443:TCP:192.168.110.11:enabled:In_HTTP_TCP_445
Click the Show button and copy your rules line by line into the Define Port Exceptions form.
This method allows you to quickly create a large number of inbound rules for the Windows firewall.
Applying Microsoft Defender Firewall Rules to Windows Computers
Now it remains to assign the Firewall-Policy policy to the OU (Organizational Unit) with the user’s computers. Locate the desired OU in the Group Policy Management console, right-click on it, and select Link an Existing GPO. Select your firewall policy from the list.
Update the Group Policy settings on your clients (gpupdate /force). Verify that the ports you specified are open on users’ computers (you can use Test-NetConnection cmdlet or Portqry tool to check for open ports).
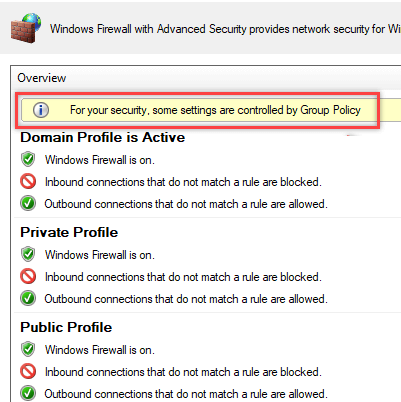
On a user’s computer, open the Control Panel -> System and Security -> Windows Defender Firewall and make sure that there is the message For your security, some settings are controlled by Group Policy and your firewall settings are used.
Now a user cannot change the firewall settings, and all rules that you have created must appear in the Inbound Rules list. Note that by default, new rules from the GPO are added to existing local firewall rules.
You can also display the current Windows Defender settings with the command:
netsh firewall show state
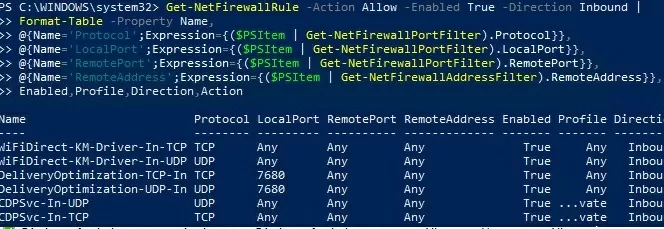
Or you can get the list of inbound rules in a table form using a PowerShell script:
Get-NetFirewallRule -Action Allow -Enabled True -Direction Inbound |
Format-Table -Property Name,
@{Name='Protocol';Expression={($PSItem | Get-NetFirewallPortFilter).Protocol}},
@{Name='LocalPort';Expression={($PSItem | Get-NetFirewallPortFilter).LocalPort}},
@{Name='RemotePort';Expression={($PSItem | Get-NetFirewallPortFilter).RemotePort}},
@{Name='RemoteAddress';Expression={($PSItem | Get-NetFirewallAddressFilter).RemoteAddress}},
Enabled,Profile,Direction,Action
How to Export and Import Firewall Rules on Windows?
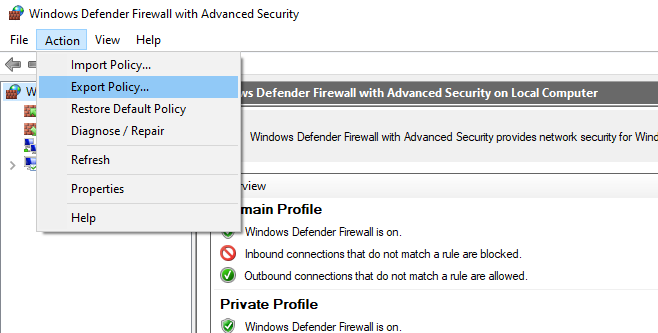
The Windows Defender Firewall Console allows you to export and import the current firewall settings to a text file. You can configure firewall rules on the reference computer and export them to the Group Policy console.
Configure the rules you need, then go to the root of the firewall snap-in (Windows Defender Firewall Monitor with Advanced Security) and select Action -> Export Policy
Your firewall rules will be exported into a WFW file, which can be imported to the Group Policy Management Editor by selecting the Import Policy option and specifying the path to the .wfw file (the current policy settings will be overwritten).
Merging Domain and Local Microsoft Defender Firewall Rules
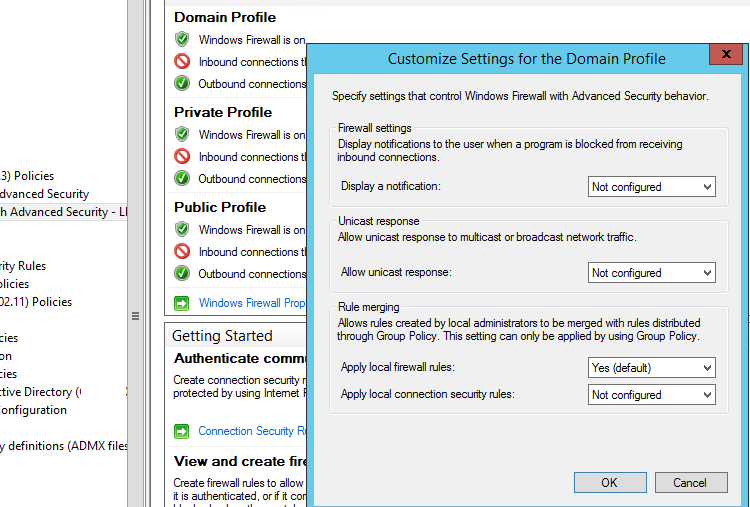
In the GPO, you can specify whether you want to allow local administrators to create their own firewall rules on their computers, and how these rules should be merged with the rules assigned through the GPO.
Open the Windows Firewall policy properties in the GPO, select the tab with the profile (Domain) and click the Customize button. Check the settings in the Rule merging section. By default, rule merging is enabled. You can force a local administrator can create their own firewall rules: select Yes (default) in the Apply local firewall rules option.
Some tips on managing the Windows Firewall using a GPO:
- Create separate GPOs with firewall rules for servers and workstations (you may need to create your own policies for each group of similar servers depending on their role. This means that the firewall rules for a domain controller, an Exchange server, a server with the Remote Desktop Services Host (RDSH) role, or Microsoft SQL Server will differ;
- You can use WMI GPO filters to target policies more precisely to clients (for example, you can apply the policy to hosts on a specific IP subnet);
- You can find out which ports must be opened for each service in the documentation on the vendor’s website. The process is quite painstaking and complicated at the first glance. However, you can finally get a working Windows Firewall configuration that allows only approved network connections and blocks the rest. From my experience, I’d like to note that you can quickly find the list of used TCP/UDP ports for most Microsoft services.
4 comments
Thanks, following your step by step process restored my firewall defender. I’ll like to ask a question, my firewall sees some of my zip as corrupt but isn’t so on my other laptop, what could be the problem?
Thanks, I didn’t feel like searching for the policy much less now that I know there is a second policy that wouldn’t work and probably would long to find the reason for it only after first breaking something trying to fix it… Standard Windows Admin.
I would not, or I should say, will not set the default of blocking inbound connections and allowing out. In a domain, computers are supposed to be in trusted zones and firewall issues are common problems everpresent in TechNet back before it was replaced for the worse. Even more important than inbound rules is not the allow anything out, in fact, not allow anything out; this is how malware receives its payload after infiltrating-in, and how telemetry both third and first party is sent back, and how Windows Update is allowed to break systems, remove features and reset settings.
I’ve ran for many years DCs, an Exchange Server, and several roles of Windows Server machines that never get updates which is supposed to make them vulnerable but in fact these machines of which some are accessible over the Internet (Exchange, ADFS), that have the firewall disabled, Defender disabled, have never been compromised because they cannot connect out on their own. DCs get DNS through DNS proxies only.
Only now I’m looking into configuring the firewall in a computer. Polish security team CQURE showed that Microsoft hardcodes some of its servers, specifically telemetry, and allows traffic regardless of firewall settings at a Microsoft event no less, so I guess I’m doing this just out of curiosity or irony maybe? than practicality now that I think about it.
fantastic write up!
Thanks For Your Helping in my company