Windows Credential Manager allows you to securely store credentials (usernames and passwords) used to access network resources, websites, and apps. You can use the credentials stored in Credential Manager to connect to network resources that support Windows authentication (NTLM or Kerberos), certificate-based authentication, or basic authentication without entering a password.
How to Open Credential Manager on Windows
Credential Manager is built into Windows and allows you to securely store the following types of credentials:
- Windows Credentials – credentials to access resources that support Windows authentication (NTLM or Kerberos). This could be credentials for mapping network drives or shared SMB folders, NAS devices, saved passwords for RDP connections, passwords for sites that support Windows authentication, etc;Windows Credential Manager does not store credentials for automatic login Windows or cached domain credentials.
- Certificate-Based Credentials – to access resources using certificates (from the Personal section of the Certificate Manager) and for smart cards;
- Generic Credentials – credentials for accessing third-party apps that are compatible with Credential Manager and support Basic authentication;
- Web Credentials – saved passwords in Edge and Internet Explorer browsers, Microsoft apps (MS Office, Teams, Outlook, Skype, etc.).
For example, if you enable the Save Password option when accessing a shared network folder, the password you enter will be saved in the Credential Manager.
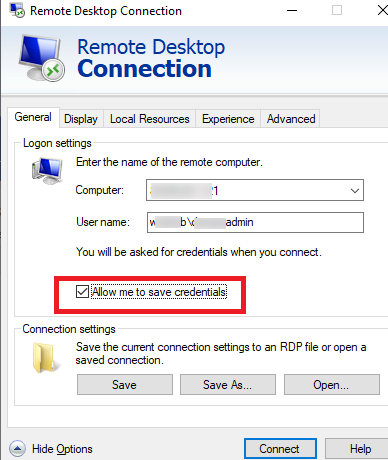
Similarly, CredManager will store an RDP host connection password that you have saved in the Remote Desktop Connection client (mstsc.exe).
runas /savecred command and used to run programs as a different user.You can access Credential Manager in Windows 10 and 11:
- from the classic Control Panel (
Control Panel\User Accounts\Credential Manager); - from the command line:
control /name Microsoft.CredentialManager
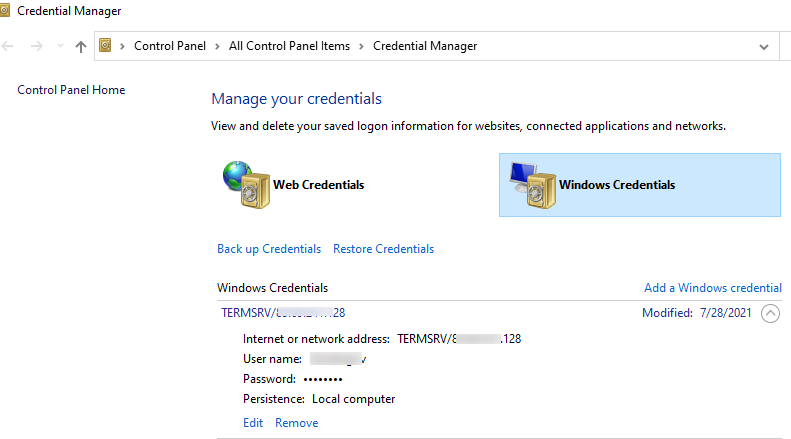
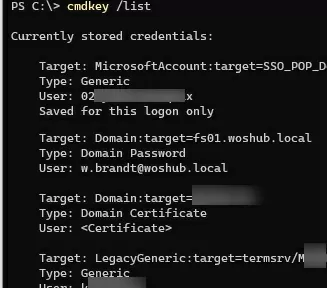
As you can see, there are two passwords in the Credential Manager that we saved earlier.
TERMSRV\hostname .Here you can add a saved credential, edit it (you cannot view a saved password in the graphic interface), or delete any of the entries.
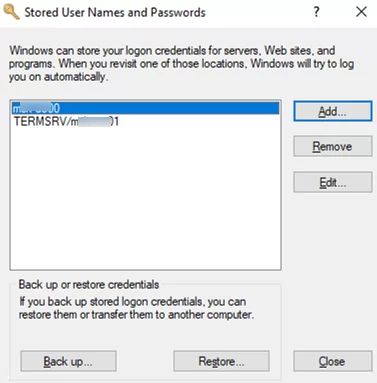
In addition, you can use the classic interface of Stored User Names and Passwords to manage saved credentials on Windows. Open in with the command below:
rundll32.exe keymgr.dll,KRShowKeyMgr
Here you can also manage your saved credentials, and backups or restores of entries in the Credential Manager (this feature can be used to move the stored credentials database to another computer).
Manage User Credentials on Windows with CMD
You can add, remove, and view saved credentials in Credential Manager from the command prompt using the cmdkey tool.
Add new credentials to access the FS01 file server:
cmdkey /add:FS01 /user:w.brandt /pass:Pa2sw0rd11
If you need to save the credentials for a domain user account:
cmdkey /add:fs01.woshub.local /user:[email protected] /pass:Pa2sw0rd11
Save the credentials for connecting to the RDP (RDS) host:
cmdkey /generic:termsrv/MUNRDS1 /user:w.brandt /pass:Pa2sw0rd11
cmdkey /add:192.168.100.25 /user:guest
To manage the hypervisor remotely from the Hyper-V Manager console, you must save the Hyper-V administrator password:
cmdkey /add:hv19 /user:Administrator /pass:HypVpaSS22
List saved credentials:
cmdkey /list
List saved credentials for a specific computer:
cmdkey /list:fs01.woshub.local
Delete previously saved credentials:
cmdkey /delete:FS01
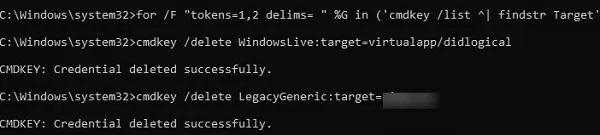
Remove any RDP passwords stored in the Credential Manager:
For /F "tokens=1,2 delims= " %G in ('cmdkey /list ^| findstr "target=TERMSRV"') do cmdkey /delete %H
Clear all stored passwords in Credential Manager with the following on-liner:
for /F "tokens=1,2 delims= " %G in ('cmdkey /list ^| findstr Target') do cmdkey /delete %H
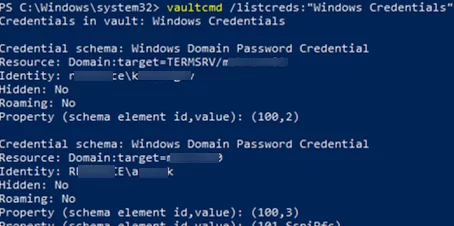
You can also manage stored credentials with vaultcmd command. List the stored credentials of type Windows Credentials:
vaultcmd /listcreds:"Windows Credentials"
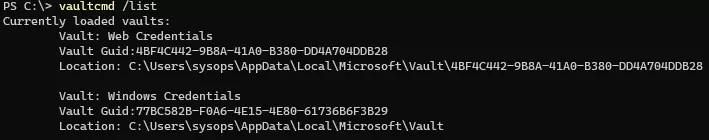
All saved passwords are stored in the secure Windows Vault. You can get the path to the Windows Credentials vault as follows:
vaultcmd /list
By default, this is %userprofile%\AppData\Local\Microsoft\Vault. The encryption key is stored in the Policy.vpol file. Passwords in .vcrd files are decrypted using the encryption key.
The VaultSvc service must be running for the Credential Manager to work:
Get-Service VaultSvc
If the service is disabled, you will receive an error when you try to access Credential Manager:
Credential Manager Error The Credential Manager Service is not running. You can start the service manually using the Services snap-in or restart your computer to start the service. Error code: 0x800706B5 Error Message: The interface is unknown.
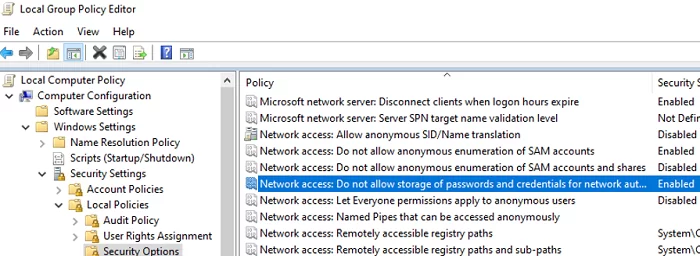
If you want to prevent users from saving network passwords in the Credential Manager, enable the Network access: Do not allow storage of passwords and credentials for network authentication GPO option under Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options.
If the user attempts to save the password to the Windows password vault, an error will now be displayed:
Credential Manager Error Unable to save credentials. To save credentials in this vault, check your computer configuration. Error code: 0x80070520 Error Message: A specified logon session does not exist. It may already have been terminated.
Accessing Windows Credential Manager from PowerShell
There are no built-in Windows cmdlets for accessing the Credential Manager vault from PowerShell. However, you can use the CredentialManager module from the PowerShell Gallery.
Install the module:
Install-Module CredentialManager
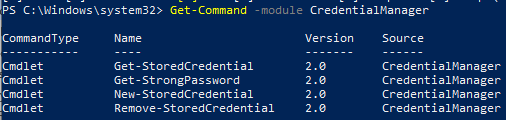
There are only 4 cmdlets in the module:
Get-StoredCredential– used to get credentials from the Windows Vault;Get-StrongPassword– to generate a random password;New-StoredCredential– to add new credentials;Remove-StoredCredential– to remove credentials.
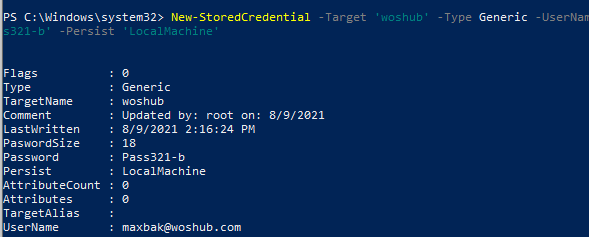
To add new credentials to the Windows Credential Manager, run this command:
New-StoredCredential -Target 'woshub' -Type Generic -UserName '[email protected]' -Password 'Pass321-b' -Persist 'LocalMachine'
Check for stored user credentials in the vault:
Get-StoredCredential -Target woshub
You can use saved passwords from Credential Manager in your PowerShell scripts. For example, I can get the saved username and password as a PSCredential object from the Windows Vault and use it to connect to Exchange Online from PowerShell.
$psCred = Get-StoredCredential -Target "woshub"
Connect-MSolService -Credential $psCred
You can also use the Get-StoredCredential cmdlet to securely retrieve saved credentials in Task Scheduler jobs.
To remove saved credentials from Windows Vault using PowerShell:
Remove-StoredCredential -Target woshub
How to Extract Saved Passwords from Windows Credential Manager
You can use the Get-StoredCredential PowerShell cmdlet to extract the plain-text password stored in Credential Manager.
List the saved credentials:
cmdkey.exe /list
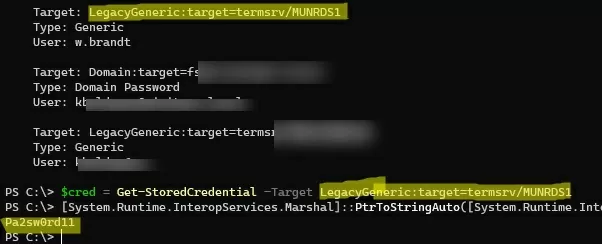
Copy the Target value for the object whose password you want to extract and paste it into the following command:
$cred = Get-StoredCredential -Target LegacyGeneric:target=termsrv/MUNRDS1
[System.Runtime.InteropServices.Marshal]::PtrToStringAuto([System.Runtime.InteropServices.Marshal]::SecureStringToBSTR( $cred.Password))
These commands display the user’s stored password in clear text.
Credman in plain text (see the example here).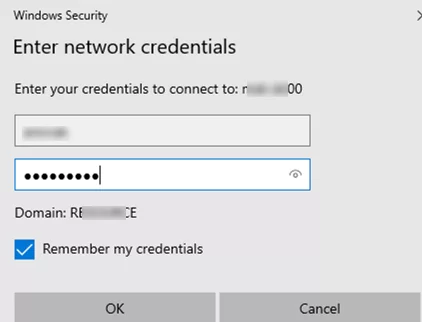
27 comments
You can convert the credential object password to plaintext by using the following.
$cred = Get-StoredCredential -Target Test1
[System.Runtime.InteropServices.Marshal]::PtrToStringAuto([System.Runtime.InteropServices.Marshal]::SecureStringToBSTR($cred.Password))
when I use this it gives me what looks like possibly password length but in foreign looking characters. I have scoured the web and am unable to find a solution
You can get stored Credential Objects and Passwords by
Get-StoredCredential -AsCredentialObject
Where do you run this command at? Powershell or CMD line? I’ve tried it in both and does not return anything but errors.
Command Prompt returns this: “‘Get-StoredCredential’ is not recognized as an internal or external command,
operable program or batch file.”
Powershell returns this in deep red on black background “The term ‘Get StoredCredential’ is not recognized as the name of a mdlet, function, script file, or operable program. ….”
Okay, I’ve gone to the top of this article and installed the module.
The commands work, but the password characters are all tiny squares with dots in them.
Have you tried converting the credential object to a plain text password like this?
$cred =Get-StoredCredential -Target test2[System.Runtime.InteropServices.Marshal]::PtrToStringAuto([System.Runtime.InteropServices.Marshal]::SecureStringToBSTR($cred.Password))
In my case, it gets the full plaintext password from the generic credential object.
Install-Module -Name CredentialManager -Force
Import-Module -Name CredentialManager
Is the solution to this problem.
Still no Passwords shown.
Any help?
Another fantastic article, as usual.
Extra thanks for mentioning the Microsoft SecretManagement and SecretStore modules. I had forgotten about those! Definitely prefer a first-party solution, and these appear to be well supported.
Thanks again!
You are welcome
as you have mentioned that the windows credentials are not visible in garphics interface. so can i see that password from command interface, if yes ! then how ?
Once stored, cred manage passwords are not displayed.
how?
This is so tantalizingly close to getting me what I need. I have an interactive application that needs to run as a specific user. If I allow Windows to save the entered credentials in Credential Manager when prompted on first run, it works. But I’m scripting the deployment of these workstations to be fully automated. If I (or someone else) has to manually type a password after deployment, it’s not fully automated, and I won’t be around to do this every time. So I’m trying to script it.
The issue is with the “target” value, which corresponds to both the display name and the “Internet or network address:” values displayed in Credential Manager. If I allow Windows to save this for me by manually going through the process of initially launching the program and typing the password, the “Target” and “Internet or network address:” values displayed in Credential Manager are in the format of “domain\username (Interactive logon)”. But if I use New-StoredCredential or cmdkey /add: to try to automate this, the target displayed in Credential Manager does not match that exact format. As a result, when I launch the program, it does not recognize/match to the stored credentials, and prompts for the password anyway. I get tripped up in CredentialManager either by the backslash in “domain\username”, or by the parentheses in “(Interactive logon)’. If I use cmdkey, I get tripped up by the spaces in the target name, even when single or double-quoted.
I keep thinking there MUST be a way to get this into credential manager in a programmatic way, but I can’t figure out the syntax on this one.
Anyone want to tackle this one?
Thank you so much @ERIC for your input it works perfectly!
You can convert the credential object password to plaintext by using the following.
$cred = Get-StoredCredential -Target Test1
[System.Runtime.InteropServices.Marshal]::PtrToStringAuto([System.Runtime.InteropServices.Marshal]::SecureStringToBSTR($cred.Password))
How do I fix error below after entering $cred = Get-StoredCredential -Target Domain:target=xxxxx
“Unable to convert Credential object without username or password to PSCredential object”
When you run the “cmdkey /list” command, you can only retrieve the passwords saved as a “Generic” type in the credential manager. If you add a credential in under the generic type, then the commands in this post work.
Hey, I am having the same issue as above “Unable to convert Credential object without username or password to PSCredential object”
I can see the credential if i run cmdkey /list under both admin and my account, and the account im interested in is “Type: Generic”
Any ideas?
Hello,
Thx a lot for sharing your knowledge, very good post.
Here is some PowerShell code I use to get CredentialManager module working on every PC on which I’m running my scripts :
Write-Host ” – Checking ‘CredentialManager’ module : ” -NoNewLine
if (Get-Module -ListAvailable -Name CredentialManager) {
Write-Host “OK” -ForegroundColor Green
} else {
Write-Host “NOK” -ForegroundColor Red
Write-Host ” – Installing ‘CredentialManager’ module … ” -NoNewLine
try {
Install-PackageProvider -Name NuGet -MinimumVersion 2.8.5.201 -Scope CurrentUser -Force -Confirm:$false | Out-Null
Install-Module CredentialManager -Scope CurrentUser -Force -Confirm:$false | Out-Null
Import-Module CredentialManager | Out-Null
Write-Host “OK” -ForegroundColor Green
} catch {
Write-Host “NOK” -ForegroundColor Red
Write-Host ” – Error : $($_.Exception.Message)” -ForegroundColor Red
}
}
Hi,
When I run the given command Get-StoredCredential I get an error:
“Get-StoredCredential : The term ‘Get-StoredCredential’ is not recognized as the name of a cmdlet, function, script
file, or operable program. Check the spelling of the name, or if a path was included, verify that the path is correct
and try again.”
I’m running PowerShell as an administrator. Do you have any other ideas what might be the cause of this?
Thank you for the great article.
I’ve gone around that problem by running:
Install-Module -Name CredentialManager -Force
Import-Module -Name CredentialManager
But now I get a warning:
“WARNING: Unable to convert Credential object without username or password to PSCredential object”
Do you know the syntax to add username and password?
$cred =Get-StoredCredential -Target LegacyGeneric:target={9B673BA3-9FF6-4933-98EA-618D876F54EA}
This gives:
“Get-StoredCredential : A positional parameter cannot be found that accepts argument ‘9B673BA3-9FF6-4933-98EA-618D876F54EA’.”
Should I replace those brackets with something else?
Have you tried placing the target into an immutable string?
as in:
$cred =Get-StoredCredential -Target ‘LegacyGeneric:target={9B673BA3-9FF6-4933-98EA-618D876F54EA}’
While I’m sure that we certainly appreciate everyone’s help here, it’s hilariously ridiculous that we (both the obviously more than one single person who needs this as well as the intelligent commenters) are all using the same Windows OS, but yet no one seems to know how to get this accomplished. I find it remarkable!
I have tried the command to retrieve the password for Target Type: Domain Password but it will return empty value.
Is there anything that i missed for retrieve Domain Password?
I’m so close, but i keep getting this error message:
PS C:\WINDOWS\system32> [System.Runtime.InteropServices.Marshal]::PtrToStringAuto([System.Runtime.InteropServices.Marshal]::SecureStringToBSTR($cred.Password))
Exception calling “SecureStringToBSTR” with “1” argument(s): “Value cannot be null.
Parameter name: s”
At line:1 char:1
+ [System.Runtime.InteropServices.Marshal]::PtrToStringAuto([System.Run …
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [], MethodInvocationException
+ FullyQualifiedErrorId : ArgumentNullException
HOW DO I FIX?
It looks like the $cred object in your case is null, or $cred.Password is empty.