Two special Windows Server DNS features can be used to automatically clean up old DNS records in Active Directory:
- DNS Aging – allows to determine the age of the dynamically registered DNS record (difference between the last timestamp and the current time)
- DNS Scavenging – automatically removes stale dynamic DNS that hasn’t been updated (used) for some time
Windows Server DNS has two types of records – dynamic and static. Dynamic records have a timestamp parameter (the time at which the DNS record was last updated). Active Windows clients update the timestamp in their DNS records at boot or every 24 hours. This parameter allows the DNS server to identify records that have not been updated for a long time and therefore have not been used.
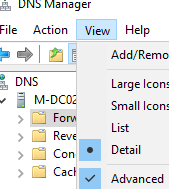
Open the DNS server management console on the AD domain controller (dnsmgmt.msc) and check the Advanced option in the View menu.
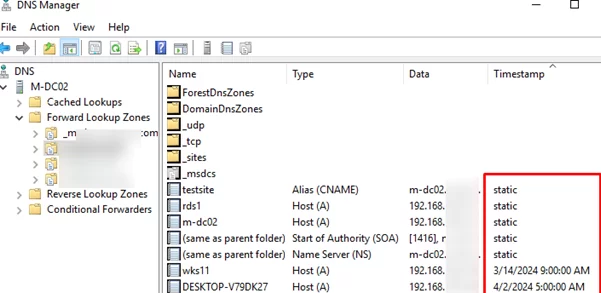
There are static and dynamic records among the zone DNS records (with time in the timestamp).
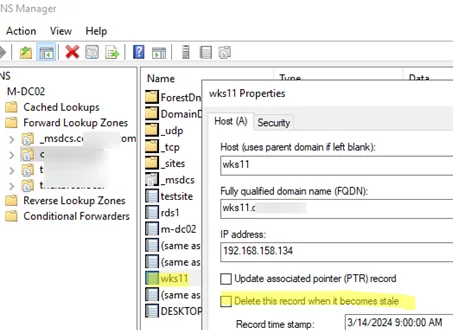
Static DNS records are not deleted automatically. Such DNS records are created by the administrator, or if the Delete this record them it becomes stale option is disabled in their settings.
Look closely at the dynamic entries in your DNS zone. Disable this option in the properties for any DNS records that should never be automatically deleted. The type of such a DNS record will change to static.
Ensure that static records are configured for all your servers, network devices, printers, scanners, and other network services.
By default, automatic scavenging for stale DNS records is disabled in Windows Server.
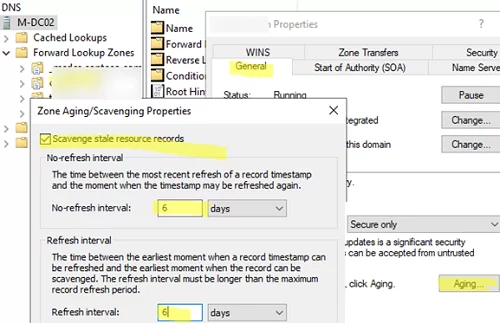
Open your DNS zone properties and click the Aging button on the General tab.
- Check the option Scavenge stale resource records.
- The No-Refresh Interval parameter sets the time interval during which the timestamp of the DNS record will not be updated (reduces DNS server load and AD replication). However, if the computer’s hostname has changed, the DNS record will be updated successfully.
- Refresh Interval – this is a time during which the DNS record timestamp can be updated.
The value for the No refresh interval should be set to half of the IP address lease time set on your DHCP server. For example, if the IP address lease time on the DHCP server is 12 days, enter 6 here. In this case, the dynamic DNS record will be considered outdated and will be purged by the scavenging job after 12 days of inactivity.
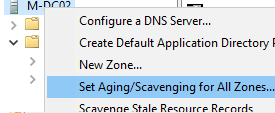
By clicking on the DNS server and selecting Set Aging/Scavenging for All Zones, the aging settings can be applied to all primary DNS zones on a domain controller.
Currently, you only have the DNS record age option configured for the zone. DNS records won’t be removed unless you have enabled the automatic cleanup in the DNS server settings.
Get-DnsServerResourceRecord -ZoneName 'contoso.com' | Select-Object hostname, timestamp, recordtype, @{Name='RecordData';Expression={$_.RecordData.ipv4address}}| Export-CSV -Csv "C:\temp\BackupDNSZoneContoso.csv" -NoTypeInformation
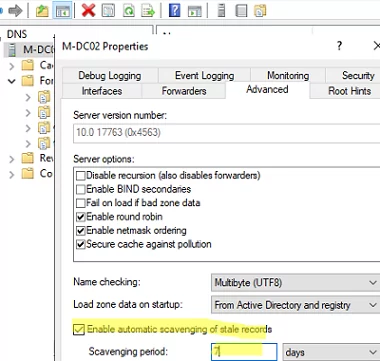
Go to the Advanced tab in the DNS server properties.
Enable the Enable automatic scavenging of status records option and specify how many days after the DNS record is marked as obsolete by the aging mechanism it should be deleted (default is 7 days). After this, the Scavenging mechanism will automatically delete old DNS records once a day.
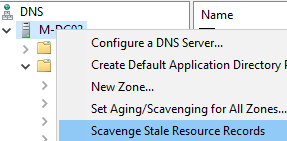
Right-click the DNS server and select Scavenging Stale Resource Records to perform the cleanup immediately. Or run the command:
Start-DnsServerScavenging -Verbose
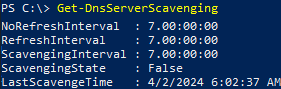
The current DNS server scavenging settings and the time of the last cleanup can be obtained using PowerShell:
Get-DnsServerScavenging
NoRefreshInterval : 7.00:00:00 RefreshInterval : 7.00:00:00 ScavengingInterval : 7.00:00:00 ScavengingState : False LastScavengeTime : 4/2/2024 6:02:37 AM