The Server Message Block (SMB) is a client-server network protocol used in Windows networks to provide remote access to shared files, printers, other network resources, and for interprocess communication. TCP port 445 is used for communication between SMB clients and servers. In this article, we’ll explore the versions of the SMB protocol available across different Windows versions (and how they relate to samba versions in Linux); how to check the SMB version in use on your computer; and how to enable/disable the SMBv1, SMBv2, and SMBv3 protocol dialects on a Windows computer (client or server).
SMB Protocol Versions in Windows
There are several versions of the SMB protocol (dialects) that have consistently appeared in new Windows versions (and Samba).
- CIFS – Windows NT 4.0
- SMB 1.0 – Windows 2000
- SMB 2.0 – Windows Server 2008 and Windows Vista SP1 (supported in Samba 3.6)
- SMB 2.1 – Windows Server 2008 R2 and Windows 7 (Samba 4.0)
- SMB 3.0 – Windows Server 2012 and Windows 8 (Samba 4.2)
- SMB 3.02 – Windows Server 2012 R2 and Windows 8.1 (partially supported in Samba)
- SMB 3.1.1 – Windows Server 2016 and Windows 10 (support for this feature was introduced in Samba 4.3, and it is now used by default)
- SMB 3.1.1 (*) – this version of SMB was introduced in Windows 11 and Windows Server 2022. It received support for SMB over QUIC, compression of SMB file traffic, and encryption with AES-256-GCM and AES-256-CCM support. Starting with Windows 11 24H2, SMB packet signing is mandatory.
SMB is a client-server protocol in which an SMB server provides access to shared resources for SMB clients.
In SMB communication, the client and server use the maximum SMB protocol version supported by both the client and the server. Use the following summary table to determine which SMB protocol version is selected when different versions of Windows interact.
| Operating System | Win 10/11, Win Server 2016/ 2019/ 2022/ 2025 | Windows 8.1, Win Server 2012 R2 | Windows 8,Server 2012 | Windows 7,Server 2008 R2 | Windows Vista,Server 2008 | Windows XP, Server 2003 and earlier |
| Windows 10 and 11, Windows Server 2016/2019/ 2022/2025 | SMB 3.1.1 | SMB 3.02 | SMB 3.0 | SMB 2.1 | SMB 2.0 | SMB 1.0 |
| Windows 8.1, Server 2012 R2 | SMB 3.02 | SMB 3.02 | SMB 3.0 | SMB 2.1 | SMB 2.0 | SMB 1.0 |
| Windows 8, Server 2012 | SMB 3.0 | SMB 3.0 | SMB 3.0 | SMB 2.1 | SMB 2.0 | SMB 1.0 |
| Windows 7, Server 2008 R2 | SMB 2.1 | SMB 2.1 | SMB 2.1 | SMB 2.1 | SMB 2.0 | SMB 1.0 |
| Windows Vista, Server 2008 | SMB 2.0 | SMB 2.0 | SMB 2.0 | SMB 2.0 | SMB 2.0 | SMB 1.0 |
| Windows XP, 2003 and earlier | SMB 1.0 | SMB 1.0 | SMB 1.0 | SMB 1.0 | SMB 1.0 | SMB 1.0 |
For example, when a Windows 8.1 client computer connects to a Windows Server 2016 file server, the SMB 3.0.2 protocol is used.
According to this table, Windows XP and Windows Server 2003 can only use SMB 1.0 to access shared files and folders on the server (this protocol is disabled by default on modern Windows versions). This means that computers running Windows XP or Windows Server 2003/R2 (no longer supported) will not be able to access shared folders on machines running newer versions of Windows.
For example, clients using Windows XP or Server 2003 will be unable to access the SYSVOL and NETLOGON folders on domain controllers or log in to Active Directory (AD) if a DC is running Windows Server 2012 R2 or a later version.
When trying to connect to a resource on a file server with SMB v1 disabled from legacy clients, an error appears:
The specified network name is no longer available
How to Check SMB Version on Windows
Run the PowerShell command to determine which SMB protocol versions (dialects) are available on a computer:
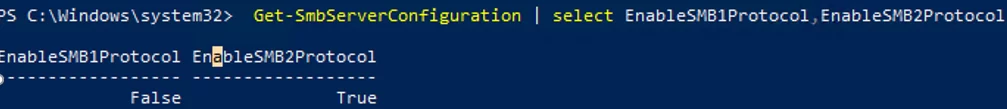
Get-SmbServerConfiguration | select EnableSMB1Protocol,EnableSMB2Protocol
This command returned that the SMB1 protocol is disabled (EnableSMB1Protocol = False), and the SMB2 and SMB3 protocols are enabled (EnableSMB2Protocol = True).
SMB client functionality is provided by the LanmanWorkstation service, while SMB server functionality is handled by the LanmanServer. Check that these services are running:
Get-Service LanmanServer,LanmanWorkstation
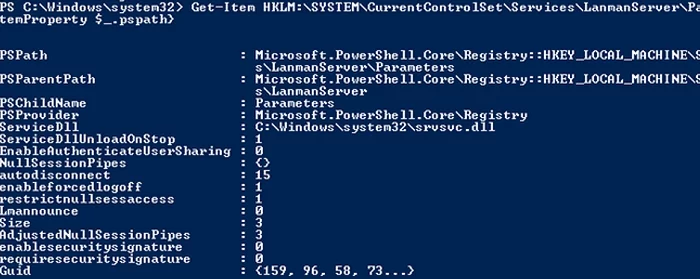
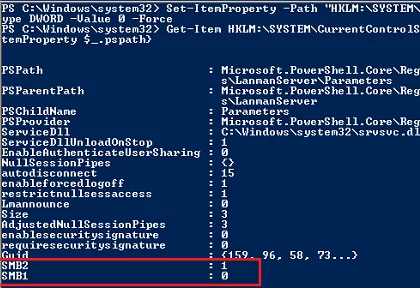
For legacy Windows versions (Windows 7, Vista, and Windows Server 2008 R2/2008), you can view the enabled SMB protocols in the registry:
Get-Item HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters | ForEach-Object {Get-ItemProperty $_.pspath}
If this registry key doesn’t contain items named SMB1 or SMB2, then both of these protocols are enabled (this is the default configuration).
In earlier versions of Windows, you could find out which SMB dialects are allowed to be used as clients:
sc.exe query mrxsmb10
SERVICE_NAME: mrxsmb10 TYPE : 2 FILE_SYSTEM_DRIVER STATE : 4 RUNNING (STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN) WIN32_EXIT_CODE : 0 (0x0) SERVICE_EXIT_CODE : 0 (0x0) CHECKPOINT : 0x0 WAIT_HINT : 0x0
sc.exe query mrxsmb20
SERVICE_NAME: mrxsmb20 TYPE : 2 FILE_SYSTEM_DRIVER STATE : 4 RUNNING (STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN) WIN32_EXIT_CODE : 0 (0x0) SERVICE_EXIT_CODE : 0 (0x0) CHECKPOINT : 0x0 WAIT_HINT : 0x0
In both cases, the services are running (STATE = 4 Running). This means that the current Windows device can connect to both SMBv1 and SMBv2 hosts.
Find Used SMB Protocol Versions with Get-SMBConnection
When communicating over the SMB protocol, the client and server negotiate and use the highest dialect version supported by both sides. Use the PowerShell cmdlet to see which SMB protocol versions clients are using to connect to an SMB server:
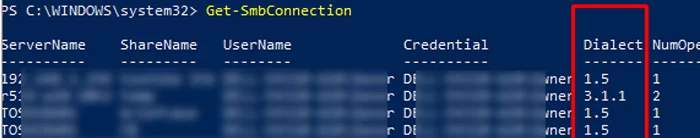
Get-SMBConnection
The SMB version that is used to connect to the remote server (ServerName) is listed in the Dialect column.
To find out if SMB encryption (introduced in SMB 3.0) is being used, run the following command:
Get-SmbConnection | ft ServerName,ShareName,Dialect,Encrypted,UserName
$ sudo smbstatus
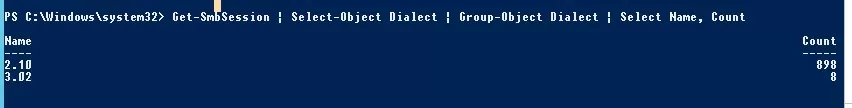
List the SMB dialects that active clients use to connect to the file server, along with the number of connections:
Get-SmbSession | Select-Object -ExpandProperty Dialect | Sort-Object -Unique
You can use PowerShell to enable auditing of the SMB versions used for the connections:
Set-SmbServerConfiguration –AuditSmb1Access $true
SMB connection events can then be queried from the Event Viewer logs using PowerShell.
Get-WinEvent -LogName Microsoft-Windows-SMBServer/Audit
Why Is SMBv1 Disabled in Newer Windows Versions?
Due to serious security issues and critical vulnerabilities, SMB protocol version 1.0 is deprecated and disabled by default in modern versions of Windows (the WannaCrypt and Petya ransomware attacks are good examples of how vulnerabilities in the SMBv1 protocol can be exploited). The legacy SMB1 protocol has been replaced by the newer and more secure SMB2 and SMB3 protocols.
Starting with Windows 10 version 809, the SMB1 client and server services are disabled by default during clean operating system installations.
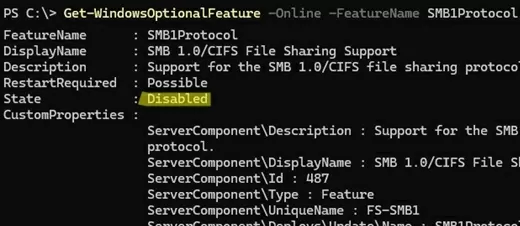
Check that SMB 1.0 is disabled using the command:
Get-WindowsOptionalFeature -Online -FeatureName SMB1Protocol
Although the legacy SMB 1.0 protocol can still be enabled on Windows devices, it is not recommended for security reasons. Disabling SMB 1 may prevent Windows from accessing shared folders on legacy devices (old NAS versions, shared network printers, Windows XP/Server 2003 devices, old Linux versions, etc.) that don’t support the newer versions of the protocol.
If there are no legacy devices left on your network that only support SMBv1, disable this protocol on all Windows computers.
How to Enable and Disable SMBv1, SMBv2, and SMBv3 on Windows
Let’s look at ways to enable and disable different SMB versions on Windows. We’ll cover SMB client and server management separately since they are different Windows components.
Windows 11, 10, 8.1, Windows Server 2025/2022/2019/2016/2012R2:
Disable SMBv1 client and server:
Disable-WindowsOptionalFeature -Online -FeatureName smb1protocol
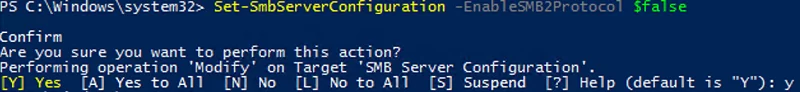
Disable SMBv1 server only:
Set-SmbServerConfiguration -EnableSMB1Protocol $false
Enable SMBv1 client and server:
Enable-WindowsOptionalFeature -Online -FeatureName smb1protocol
Enable only SMBv1 server:
Set-SmbServerConfiguration -EnableSMB1Protocol $true
Disable SMBv2 and SMBv3 server:
Set-SmbServerConfiguration -EnableSMB2Protocol $false
Enable SMBv2 and SMBv3 server:
Set-SmbServerConfiguration -EnableSMB2Protocol $true
Windows 7, Vista, and Windows Server 2008 R2/2008:
Disable SMBv1 server:
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" SMB1 -Type DWORD -Value 0 –Force
Enable SMBv1 server:
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" SMB1 -Type DWORD -Value 1 –Force
Disable SMBv1 client:
sc.exe config lanmanworkstation depend= bowser/mrxsmb20/nsi
sc.exe config mrxsmb10 start= disabled
Enable SMBv1 client:
sc.exe config lanmanworkstation depend= bowser/mrxsmb10/mrxsmb20/nsi
sc.exe config mrxsmb10 start= auto
Disable SMBv2 server:
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" SMB2 -Type DWORD -Value 0 -Force
Enable SMBv2 server:
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" SMB2 -Type DWORD -Value 1 –Force
Disable SMBv2 client:
sc.exe config lanmanworkstation depend= bowser/mrxsmb10/nsi
sc.exe config mrxsmb20 start= disabled
Enable SMBv2 client:
sc.exe config lanmanworkstation depend= bowser/mrxsmb10/mrxsmb20/nsi
sc.exe config mrxsmb20 start= auto
Regardless of the Windows version, you can disable the SMBv1 server on all domain-joined computers by deploying the following registry parameter through the GPO:
- Key: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters
- Name: SMB1
- Type: REG_DWORD
- Value: 0
Set the registry parameter SMB2=0 in order to disable the SMBv2 server.
To disable the SMBv1 client, deploy the following registry item:
- Key: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\mrxsmb10
- Name: Start
- Type: REG_DWORD
- Value: 4
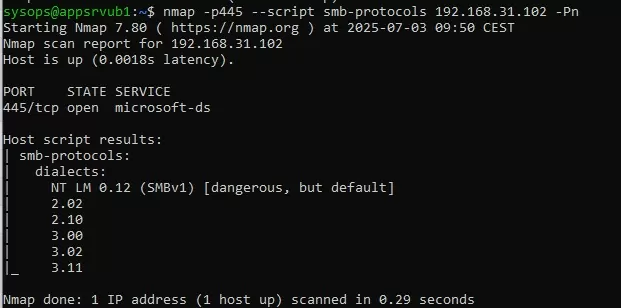
How to Detect Which SMB Versions Are Enabled on Network Computers
Nmap can be used to scan the network and identify devices that are using the insecure SMBv1 protocol version. The following command will scan the specified IP subnet and display the SMB versions on the devices.
nmap -p445 --script smb-protocols 10.1.2.0/24 -Pn
In an Active Directory domain environment, this PowerShell script can be used to get information about the enabled SMB versions on computers:
$serverList = Get-ADComputer -Filter {(OperatingSystem -like "Windows Server*") -and (Enabled -eq $true)} | Select-Object -ExpandProperty Name
$results = @()
foreach ($server in $serverList) {
$serverStatus = Test-Connection -ComputerName $server -Count 1 -Quiet
if ($serverStatus) {
$smbStatus = Invoke-Command -ComputerName $server -ScriptBlock {
Get-SmbServerConfiguration | Select-Object EnableSMB1Protocol, EnableSMB2Protocol
}
$results += [PSCustomObject]@{
ServerName = $server
IsOnline = $true
SMBv1Enabled = $smbStatus.EnableSMB1Protocol
SMBv2Enabled = $smbStatus.EnableSMB2Protocol
}
}
else {
# If the server is unavailable:
$results += [PSCustomObject]@{
ServerName = $server
IsOnline = $false
SMBv1Enabled = $null
SMBv2Enabled = $null
}
}
}
$results | Format-Table -AutoSize
# Saving results to a CSV file
$results | Export-Csv -Path "C:\GetAD-SMB-Status.csv" -NoTypeInformation

22 comments
your post save my day!!! thank u, i’m gonna reference it on my blog!!!
I have looked everywhere on the web to resolve this issue. THANK YOU!
Thank you! Got this issue after patching and it worked fine.
Thank you! Saved my day!
How come I have a windows server 2012 r2 with smb1 installed but not visible in dependencies and I can still access it from windows server 2003 ?
If SMB1 diver is running, you can access Windows 2012 R2 from 2003 client:
sc query mrxsmb10
E_NAME: mrxsmb10
TYPE : 2 FILE_SYSTEM_DRIVER
STATE : 4 RUNNING
You don’t need dependency with smb v1, so only v2 is enable in lan manager : this is more secure
`
echo Check SMB protocoles :
echo —————————————
echo.
for %%V in (1 2) do (
for /F %%L in (‘sc qc lanmanworkstation ^| find “mrxsmb%%V0″‘) do (
echo – Lan manager depends of SMB V%%V
for /F %%S in (‘sc query mrxsmb%%V0 ^| find /C “RUNNING”‘) do (
IF %%S EQU 1 (
echo OK, SMB V%%V service is running
) else (
echo.
echo ********************************************************************************************************
echo SMB V%%V is not running, script is ending
echo Type these commands as administrator :
echo.
echo C:^> sc qc lanmanworkstation ^(to show dependances, mrxsmb10 = SMB V1, mrxsmb20 = SMB V2^)
echo C:^> sc config lanmanworkstation depend= bowser/mrxsmb20/nsi ^(In order to disable SMB V1^)
echo C:^> sc config mrxsmb10 start= disabled
echo C:^> sc config mrxsmb20 start= auto ^(to start SMB V2 with system^)
echo Then restart computer
echo ********************************************************************************************************
goto END_SCRIPT
)
)
)
)
`
2012 onwards;
Check it’s not disabled via Powershell too:
To Check:
Get-SmbServerConfiguration | Select EnableSMB1Protocol,
If it say ‘False ‘then Ennable:
Set-SmbServerConfiguration -EnableSMB1Protocol $false
Thank you for your comment. Indeed, SMB1 server protocol is available by default on Windows Server 2012 R2. I updated the article
Perfect, just what the doctor ordered. Saved my life and time.
If you are disabling/removing the SMB1 protocol then you need to make the necessary changes in the registry by enabling the dependencies of SMB 2.0 in Windows Server 2012 R2 through the registry otherwise your shares will stop working. Go to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer and change the value of DependOnService parameter from SamSS Srv to SamSS Srv2. Need to restart the server after this change.
Thanks
Great articles, but you might want to include a reference to the following group policies:
– “Network security: LAN Manager authentication level” change to Send LM & NTLM responses
– “Network security: Minimum session security for NTLM SSP based (including secure RPC) servers “ – Disable Require 128-bit encryption option
– “Network security: Minimum session security for NTLM SSP based (including secure RPC) clients “ – Disable Require 128-bit encryption option
In my case crucial to make it work (win2012 r2)
You the best!! always your posts are rich and very clear to understand!!
Many thanks!!
Thank you man !! very usefull and clear guide in Windows smb labirint.. your detailed instruction work !! i just connected an smb1 printer on 2012 r2.
[…] How to Check, Enable or Disable SMB Protocol Versions on Windows? | Windows OS Hub (woshub.com) […]
Your article says:
This command returned that the SMB1 protocol is disabled (EnableSMB1Protocol = True), and the SMB2 and SMB3 protocols are enabled (EnableSMB1Protocol = False).
But the value of EnableSMB1Protocol is actually *False* and the value of *EnableSMB2Protocol* is True
Unless I’m mistaken, your explanation is topsy-turvy
Great article. Howver, I get different results using diffrent commands. Perhaps I am misisng something
1. sc.exe query mrxsmb10
Error which means does not exist which indicates SMB is not running
2. Sc.exe query mrxsmb20 is running.
3. Get-Item HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters
I get no SMB keys and you state this means SMBv1 amd SMBc2 are enabled by default
4. Gwt-WindowsFeature *smb*
Shows SMB is not installed
5. Get-smbServerConfiguration | select enableSMBProtocol, EnableSMB2Protocl | ft -autosize
EnableSMB1Protocol = True
However,
DISM /online /get-feature /format:table find “SMB1Protocol” returns EnableSMB1Protocol =Disabled.
DISM is accurate.
I feel the most reliable command is the one you mention below:
Hello can you guide me how to enable SMB3 on windows server 2019 please. (server-side)
Domain controllers 2012 R2 have SMB1 disabled by default.
To enable SMB 1.0 support in Windows Server 2012 R2, open the Registry Editor, go to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer and change the value of DependOnService from SamSS Srv2 to SamSS Srv.
Been Googling and failing for hours. Was trying to access and copy old camcorder files from an old XP machine to a not-quite-as-old Win7 machine. I quickly understood the issue was with SMB1 (XP) and SMB2 (Win7). I could see shared folders in XP belonging to Win7 but not the other way around (Error: 80070035). Of course I realize I could simply copy the desired file(s) in XP to a visible shared folder belonging to Win7. But not the point (XP machine temporarily on the floor, in a corner, and I’m 75 and don’t like to be inconvenienced). I knew all I had to do was enable SMB1 in Win7. Your article is vastly comprehensive, and seems to cover all scenarios and OS steppings. So very grateful someone with your knowledge and expertise took the time to compile and share this information AND How-To’s. My issue resolved.
After “optimizing” my system with the help of ChatGPT & Co I totally messed up my SMB configuration. Was about to reinstall everything before I found this page. Pasted some of the commands to deavtivate SMB1 and activate SMB2 and everything is running again!
But I think one line is probably wrong:
Enable SMBv2 client:
sc.exe config lanmanworkstation depend= bowser/mrxsmb10/mrxsmb20/nsi
should probably read
sc.exe config lanmanworkstation depend= bowser/mrxsmb20/nsi
if you don’t want SMB1 or removed it