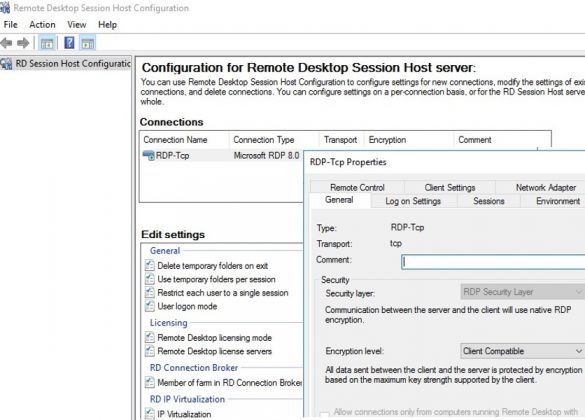
Many administrators of Windows terminal servers noticed that starting from Windows Server 2012, the management snap-ins tsadmin.msc (Remote Desktop Services Manager) and tsconfig.msc (Remote Desktop Session Host Configuration) are missing…
Windows Server 2019: Installation and Configuration Tutorials
What Others Are Reading in Windows Server 2019
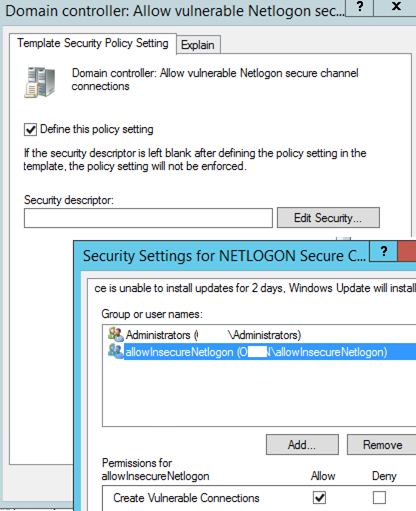
Zerologon (CVE-2020-1472): Critical Active Directory Vulnerability
In August 2020, Microsoft released an update to fix a critical Windows Server vulnerability in Active Directory — CVE-2020-1472 (more known as Zerologon) . This update was successfully installed on…
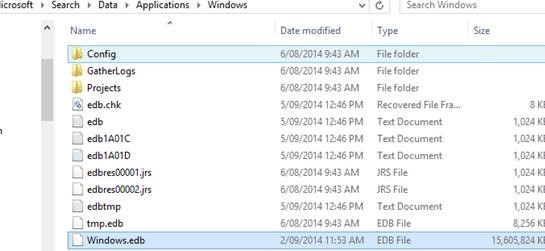
Reduce Large Windows.edb (Windows.db) File Size
The Windows.edb file (Windows.db in Windows 11) is the location of the index database for the Windows Search service. The search index allows users to quickly search for files, emails…
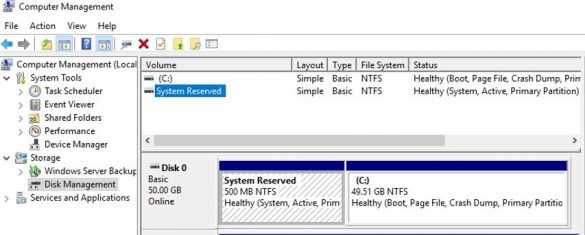
During a clean OS install, Windows Installer creates a special System Reserved Partition (SRP) on the MBR disk partition table. This is a hidden partition with the NTFS file system,…
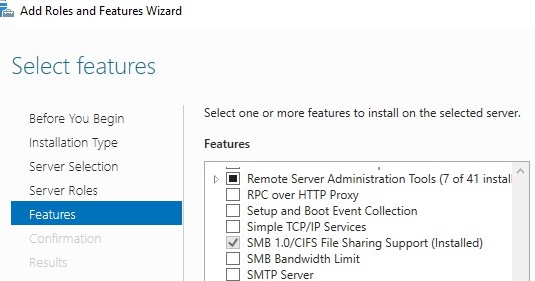
How to Enable or Disable SMB 1.0 in Windows 10/11 and Windows Server
The Server Message Block (SMB) 1.0 file-sharing protocol is disabled by default in the latest versions of Windows 11 and 10 and in Windows Server 2019/2022. This version of the…
How to Install Only Specific Apps in Office 2021/2019 or Office 365
When you install Microsoft Office 2021, 2019, 2016. or Microsoft 365 Apps for Business (ex-Office 365), you cannot choose to install individual Office apps, change a path to the installation…
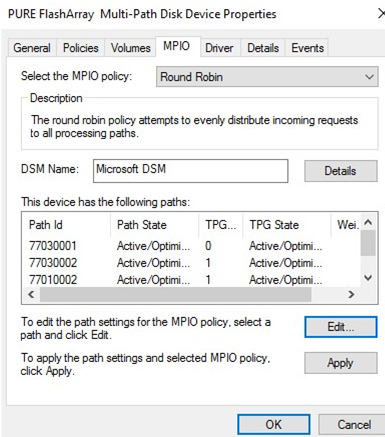
How to Enable and Configure MPIO on Windows Server
In this article we will consider how to install and configure MPIO on Windows Server 2016/2012 R2. MPIO (Multi—Path Input Output) is a technology that allows to build fault-tolerant transport to a data storage system…
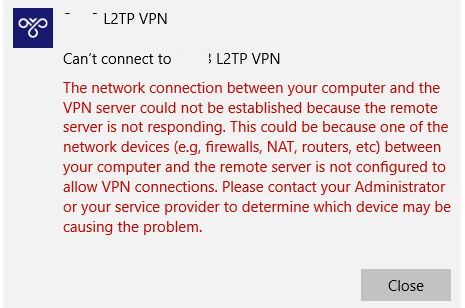
How to Connect L2TP/IPSec VPN Server From Windows
In this article, we will look at the most common causes of errors when connecting to an L2TP/IPSec VPN server from Windows 10/11 or Windows Server 2019/2016. If you cannot…
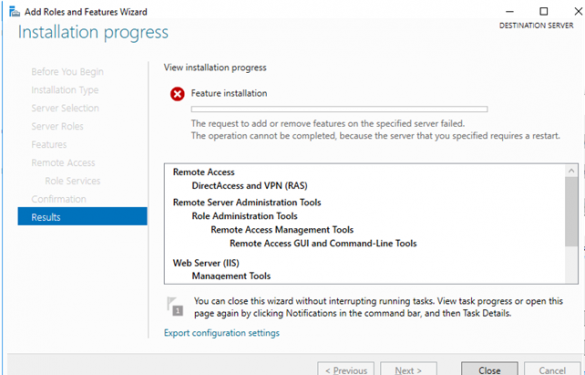
Unable to Add/Remove Role: Windows Server Requires Restart
When installing any role or feature on Windows Server 2016, an error appears that the server requires a restart: “The request to add or remove features on the specified server…
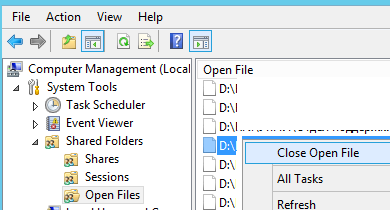
How to View and Close Open Files on Windows Server
A Windows file server admin can list the files that are open in a shared folder and force locked files to close. If a user opens a file in a…