The built-in Windows Remote Desktop client (mstsc.exe) allows you to save the username and password used to connect to the remote computer. Thanks to this, the user doesn’t need to enter a password each time to connect to a known Remote Desktop host. In this article, we’ll look at how to allow using saved credentials for RDP connections in Windows, and what to do if users cannot use saved passwords for Remote Desktop connections (the password is requested every time)
Allow Saved Credentials Delegation for RDP Connection via GPO
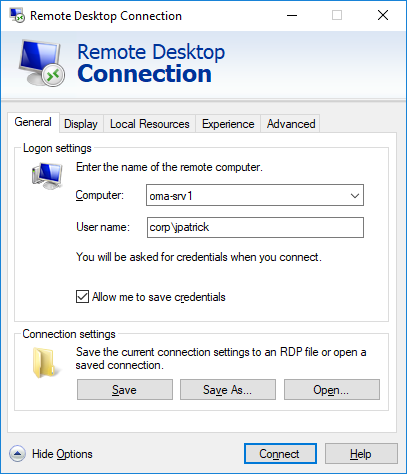
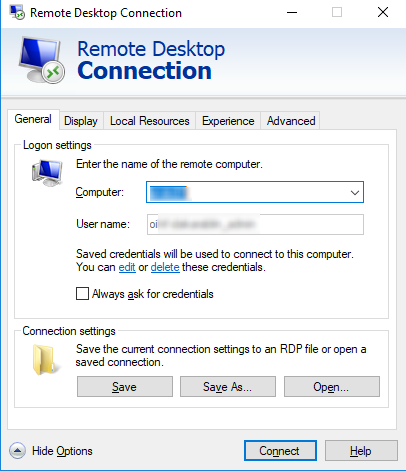
By default, Windows allows users to save their passwords for RDP connections. To do it, a user must enter the name of the RDP computer, the username and check the box “Allow me to save credentials” in the Remote Desktop Connection (mstsc.exe) client window. After a user has clicked the “Connect” button, the RDP server asks for the password and the Windows saves it to the Credential Manager (not to the .RDP file).
The next time you connect to a remote RDP host under the same user, the client will automatically get the saved password from the Windows Credential Manager and use it for RDP authentication.
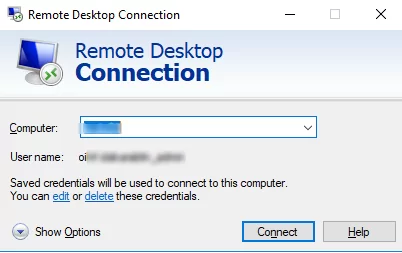
If there is a saved password for this computer, the following message will appear in the RDP client window:
Saved credentials will be used to connect to this computer. You can edit or delete these credentials.
By default, Windows doesn’t allow a user to use a saved RDP password (credentials) to connect from a computer joined to an Active Directory domain to a host that is in another domain or workgroup. Although the connection password is stored in Credentials Manager, Windows does not allow it to be used and requires the user to enter the password each time. Also, Windows prevents you from using the saved RDP password if you connect with your local account instead of your domain one.
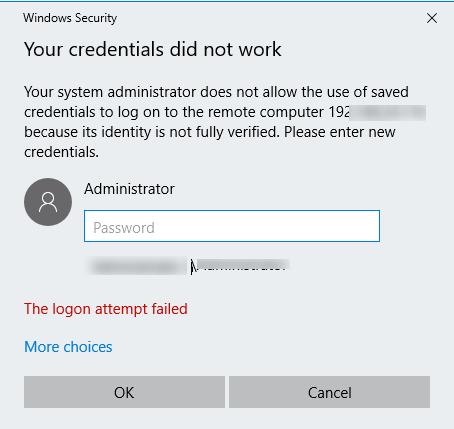
In this case, if you try to connect using the saved RDP password, this error message appears:
Your credentials did not work Your system administrator does not allow the use of saved credentials to log on to the remote computer CompName because its identity is not fully verified. Please enter new credentials.
Windows considers the connection insecure since there is no trust between this computer and the remote computer in another domain (or a workgroup).
You can change these settings on the computer you are trying to establish RDP connection from:
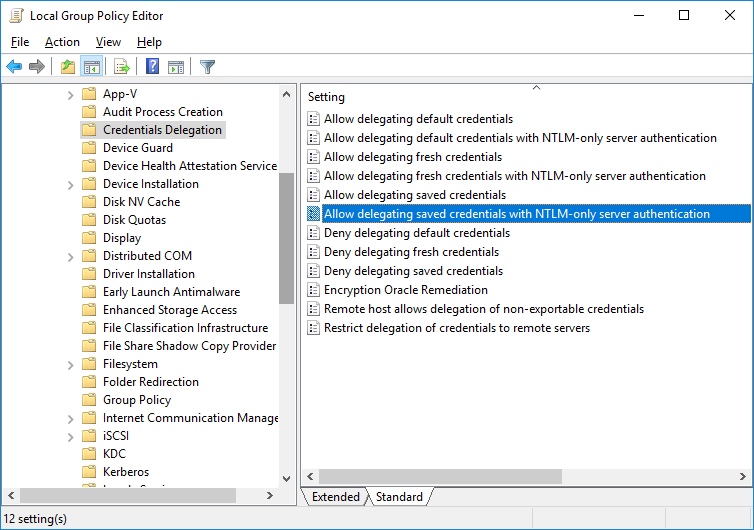
- Open the Local Group Policy Editor by pressing
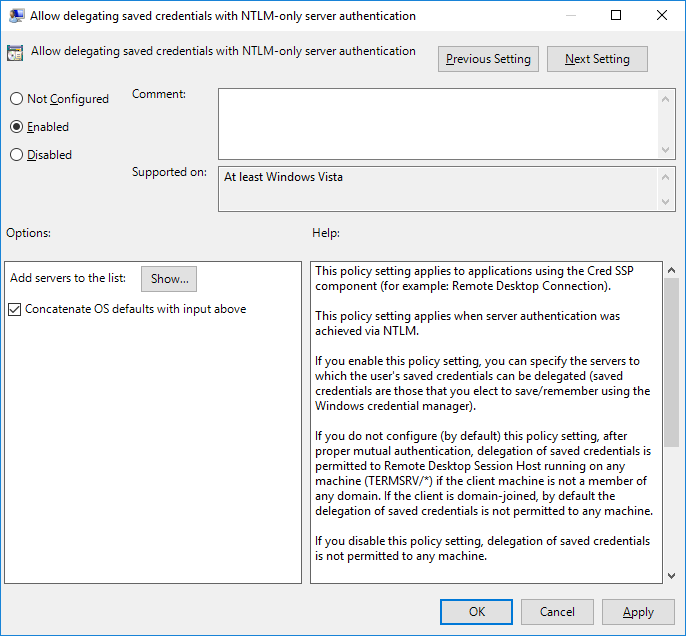
Win + R-> gpedit.msc; - In the GPO editor, go to Computer Configuration –> Administrative Templates –> System –> Credentials Delegation. Find the policy named Allow delegating saved credentials with NTLM-only server authentication;
- Enable the policy and click Show;
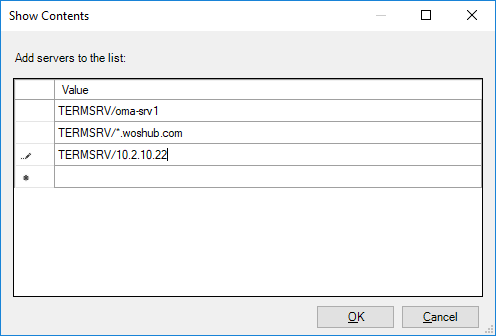
- Specify the list of remote hosts that are allowed to use saved credentials when accessed over RDP. The list of remote computers must be specified in the following format:
TERMSRV/server1— allow to use saved credentials to access a specific computer/server over RDP;TERMSRV/*.woshub.com— allow to establish RDP connections with saved credentials to all computers in the woshub.com domain;TERMSRV/*— allow using a saved password to connect to any remote computer.Tip. Be sure to type theTERMSRVkeyword in uppercase. The computer name must exactly match the one you specified in the RDP client connection field.
- Similarly, enable and add your TERMSRV/ values to the Allow Delegating Saved Credentials policy;The following registry settings correspond to the above GPO options:
Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CredentialsDelegation] "AllowSavedCredentialsWhenNTLMOnly"=dword:00000001 “AllowSavedCredentials”=dword:00000001 [HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CredentialsDelegation\AllowSavedCredentialsWhenNTLMOnly] "1"="TERMSRV/*" [HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CredentialsDelegation\AllowSavedCredentials] "1"="TERMSRV/*" [HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Policies\Microsoft\Windows\CredentialsDelegation] “AllowSavedCredentialsWhenNTLMOnly”=dword:00000001 “AllowSavedCredentials”=dword:00000001 [HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Policies\Microsoft\Windows\CredentialsDelegation\AllowSavedCredentialsWhenNTLMOnly] "1"="TERMSRV/*" [HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Policies\Microsoft\Windows\CredentialsDelegation\AllowSavedCredentials] "1"="TERMSRV/*"
- Check if the following option is disabled Network access: Do not allow storage of passwords and credentials for network authentication (Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options). If this setting is enabled, the user will receive an error when attempting to save the password to the Credential Manager vault:
Credential Manager Error Unable to save credentials. To save credentials in this vault, check your computer configuration. Error code: 0x80070520 Error Message: A specified logon session does not exist. It may already have been terminated.
- Check that the Deny delegating saved credentials policy is disabled (or not configured). Deny GPO policies take precedence over allow ones;
- Save the changes and update GPO settings using this command:
gpupdate /force
Now, when connecting to the RDP host, the mstsc client will be able to use your saved credentials.
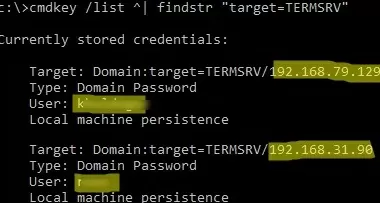
You can list saved passwords for RDP connections with the command:
cmdkey /list ^| findstr "target=TERMSRV"
To clear saved connection passwords, run the command:
For /F "tokens=1,2 delims= " %G in ('cmdkey /list ^| findstr "target=TERMSRV"') do cmdkey /delete %H
You can change the RDP saved credentials policy only on the local computer using the Local Group Policy Editor. If you want to apply these settings on multiple computers in the domain, use the domain GPO configured using the gpmc.msc (Group Policy Management) console.
Why Windows Does Not Save Remote Desktop Credentials?
If you have configured Windows following the instructions above, but your RDP client still prompts you to enter a password each time you try to connect, it is worth checking the following:
- Click “Show Options” in the Remote Desktop Connection window and make sure that “Always ask for credentials” option is not checked;
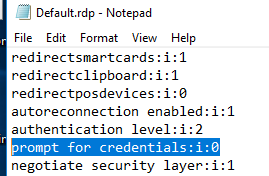
- If you are using an .RDP file for connection, make sure that the value of ‘prompt for credentials’ parameter is 0 (
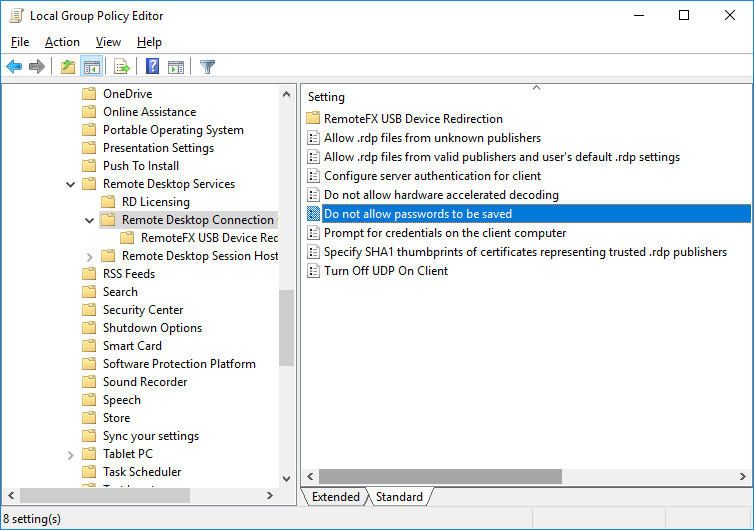
prompt for credentials:i:0); - Open the Local GPO Editor (
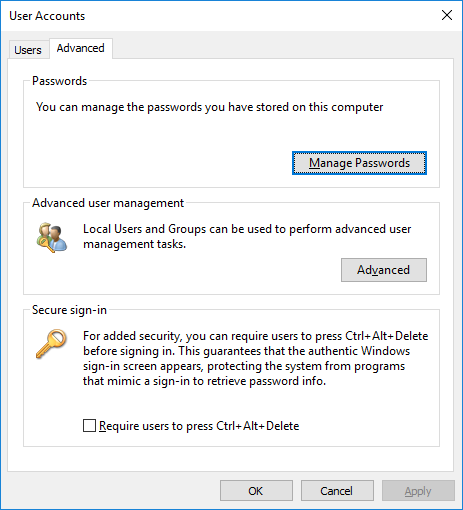
gpedit.msc) and go to Computer Configuration -> Administrative Templates -> Windows Components -> Remote Desktop Services -> Remote Desktop Connection Client. The Do not allow passwords to be saved and Prompt for credentials on the client computer” options must be not set or disabled. Also, make sure that this policy setting is disabled in the resulting Group Policy on your computer (you can create an HTML report with the applied GPO settings using the gpresult command); - Delete all saved passwords from the Windows Credential Manager. Type
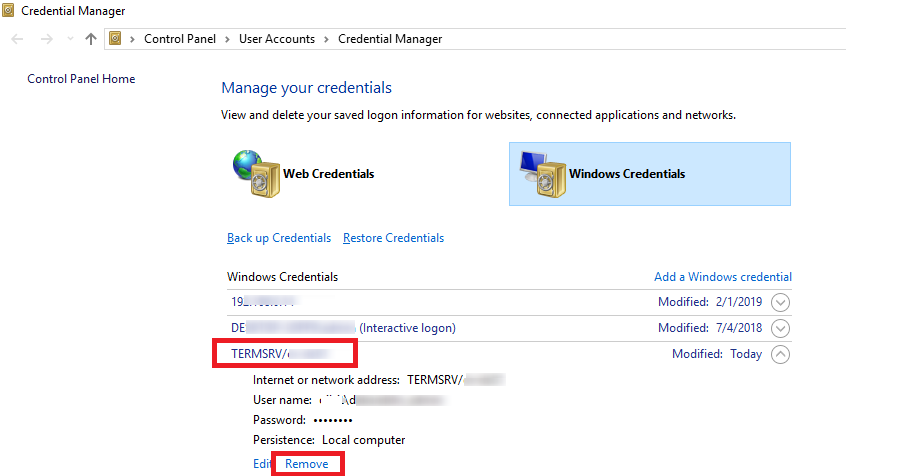
control userpasswords2and in the User Accounts window go to the Advanced tab and click Manage Passwords; - In the next window, select Windows Credentials. Find all saved RDP passwords and delete them (they start with
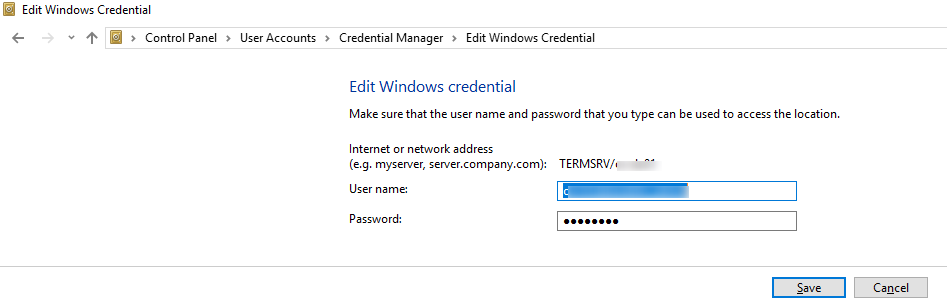
TERMRSV/…).In this window you can manually add credentials for RDP connections. Please note that the name of an RDP server/computer must be specified in theTERMRSV\server_name1format. Don’t forget to delete saved passwords when you clear the RDP connection history on your computer. - You won’t be able to logon with the saved RDP credentials if the remote server has not been updated for a long time, and when trying to connect to it, the CredSSP encryption oracle remediation error appears.
After that, users will be able to use their saved passwords for RDP connections.
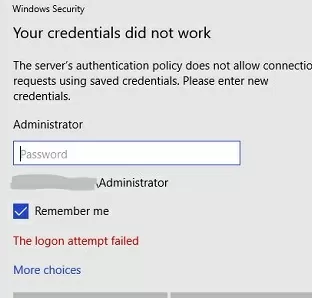
The Server’s Authentication Policy Doesn’t Allow Connection with Saved Credentials
When connecting to an RDP host or RDS farm using saved credentials, an error may appear:
Windows Security Your credentials did not work The server’s authentication policy does not allow connection requests using saved credentials. Please enter new credentials.
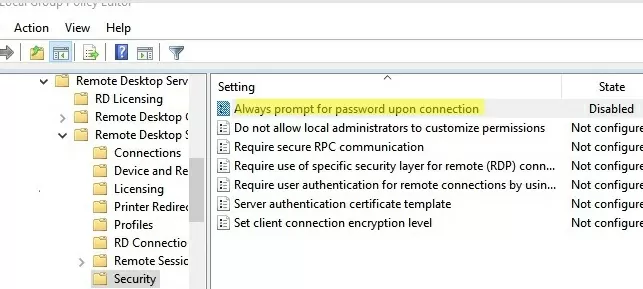
In this case, you need to disable the GPO option “Always prompt for password upon connection” on the remote server (Computer Configuration -> Administrative Templates -> Windows Components -> Remote Desktop Services -> Remote Desktop Session Host -> Security).
If this policy is enabled, the RDP host always prompts the client for a password to connect.
You can disable this option through the registry:
REG add "HKLM\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services" /v fPromptForPassword /t REG_DWORD /d 0 /f
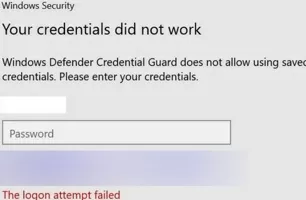
Windows Defender Credential Guard Does Not Allow Saved Credentials
After updating to Windows 11 22H2, users began to complain that they cannot use saved passwords for RDP connections:
Windows Security: Your credentials did not work Windows Defender Credential Guard does not allow using saved credentials. Please enter your credentials.
Windows Defender Remote Credential Guard (which appeared on Windows 10 1607) is supposed to protect your credentials for RDP connections. By default, Windows 11/10 22H2 only allows saved credentials to be used when using Kerberos authentication on the RDP host. If you can’t use Kerberos (the domain controller isn’t available, or you’re connecting to a host in a workgroup), the Remote Credential Guard blocks NTLM authentication.
You can solve this problem by disabling the Credential Guard through the registry:
New-ItemProperty -Path "HKLM:\System\CurrentControlSet\Control\LSA" -Name "LsaCfgFlags" -PropertyType "DWORD" -Value 0 -Force
13 comments
i follow your step but still need password
Same for me. Still need to type in password.
I always could use saved passwords. But then suddenly some weeks ago, it didn’t work any more. Certainly with some Windows update
after i test again, my problem is after join domain i cant save my credential but if workgroup i can save my RDP cred. my GPO on server not yet apply to new domain user
Sorry to disappoint, but although this post may have been valid in October of 2019, it no longer works.
Some “helpful” update to Windows 10 has made this not work. Like others above have said, “suddenly it doesn’t work any more”.
Call Bill Gates.
This got me where I needed to go – thanks a million
hmmmm my problem is that i have two accounts on my server and problem with RDP as it just save only one account like if i enter account1 : password it will save it and when i enter account2 : password then it will erase account1 details , so i wish is there any fix around to save multiple account ?
thanks
Tyson try creating a 2nd saved RDP Connection and just give them a different name each one with one specific username / password and that should work?
Hi.
Thanks, Brand new Windows10 Pro pc with all the latest updates in our AD wouldn’t save the password the first solution worked perfectly for it.
Cheers
1. Hit Start –> Run and type “gpedit.msc”.
2. Navigate to Local Computer Policy –> Computer Configuration –> Administrative Templates –> System –> Credentials Delegation.
3. Double click the policy “Allow Delegating Default Credentials with NTLM-only Server Authentication”.
4. Set the policy to “Enabled”.
5. Click the Show button and enter the string “TERMSRV/*” into the list. You can also be more specific here in case you don’t want to allow the use of saved credentials with all remote machines but rather just a select few.
6. Click OK twice to close the policy. Repeat steps 3–6 for the following policies:
1. “Allow Delegating Default Credentials”
2. “Allow Delegating Saved Credentials with NTLM-only Server Authentication”
3. “Allow Delegating Saved Credentials”
I have had success by deleting the Windows Credential and creating a Generic Credential instead.
I’ve replaced the windows credential with generic one, and it is worked fine.
How to save rdp creds in Remote Desktop Connection manager?
Thank you so much